Overview
Cisco asa provide 3 method for accessing via remote.
- Telnet
- SSH
- HTTP via ASDM
by default all of those type is disabled, in this section i will show you how to configure and enable this 3 method.
Topology
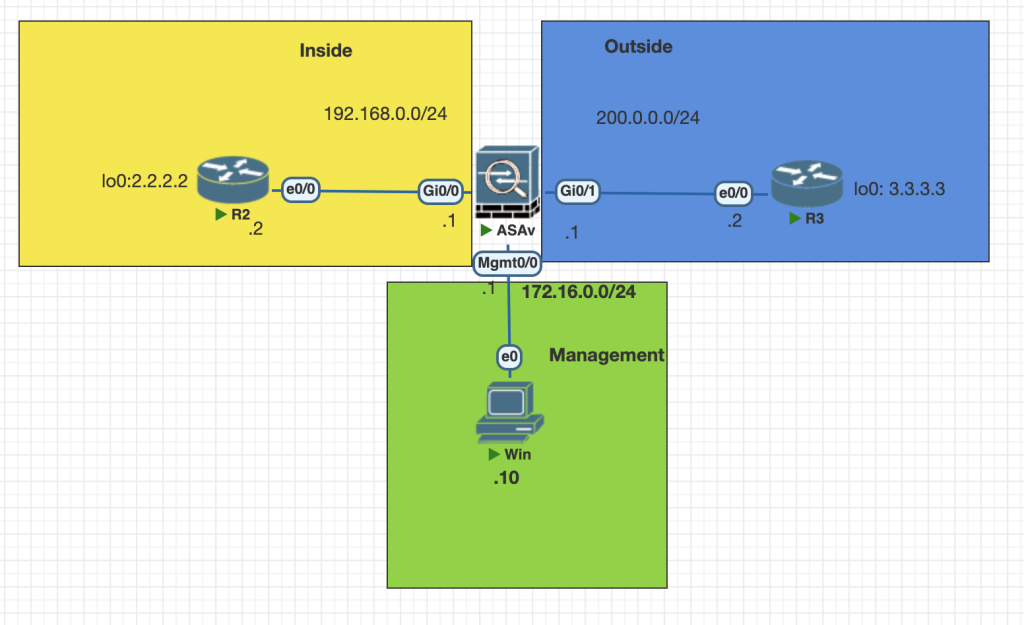
Testing Scenario
- Enable Telnet access from R2 IP 192.168.0.2 to ASA 192.168.0.1
- Enable SSH access from R3 IP 200.0.0.2 to ASA 200.0.0.1
- Enable HTTP access via ASDM from Win Server IP 172.16.0.10
Configuration
Enable Telnet Access from R2 to ASA
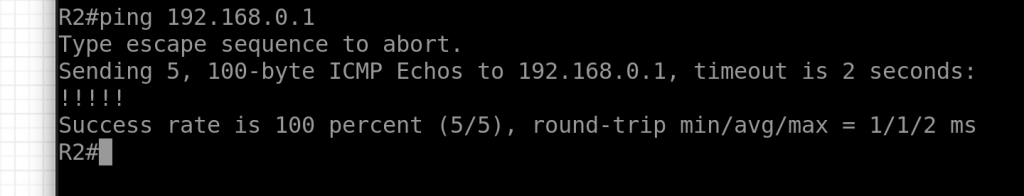
- verify connection ping is work from R2 to ASA.
- configure telnet ASA
password cisco
telnet 192.168.0.2 255.255.255.255 INSIDE3. Verification telnet from R2 login with password cisco
telnet 192.168.0.1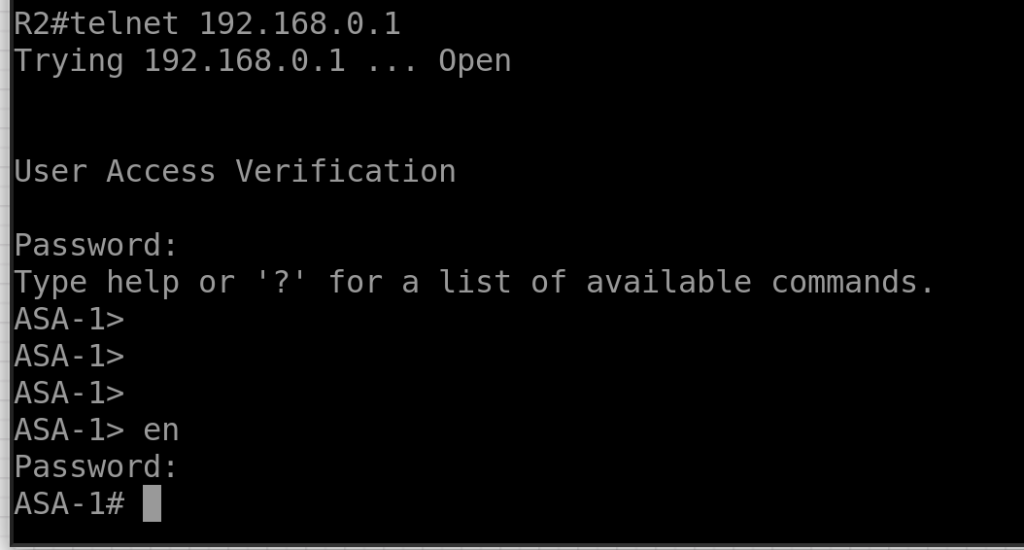
Enable SSH access from R3 to ASA
the configuration is follow
conf t
username cisco password cisco # create username
crypto key generate rsa # generate ssh key
aaa authentication ssh console LOCAL # define from where ASA will lookup the username
ssh key-exchange group dh-group14-sha1 # change the ssh key be stronger
ssh 200.0.0.2 255.255.255.255 OUTSIDEverify login via ssh from R3
ssh -l cisco 200.0.0.1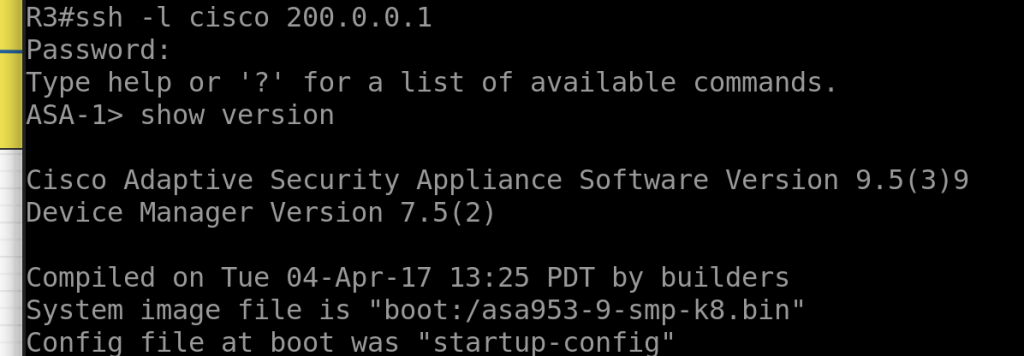
Enable HTTP ASDM From PC to ASA
To configure HTTP and access the ASA via ASDM we configure with this command.
interface Management0/0
management-only
nameif management
security-level 100
ip address 172.16.0.1 255.255.255.0
# enable http access
http server enable
http 172.16.0.2 255.255.255.0 managementaccess the cisco ASA device from ASDM client with username and password blank (default credential).
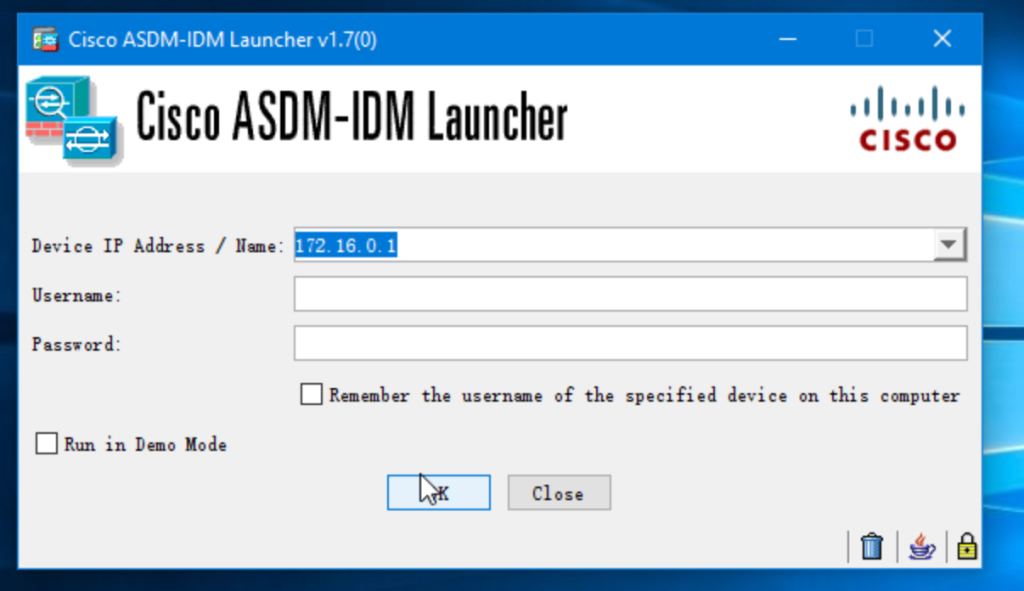
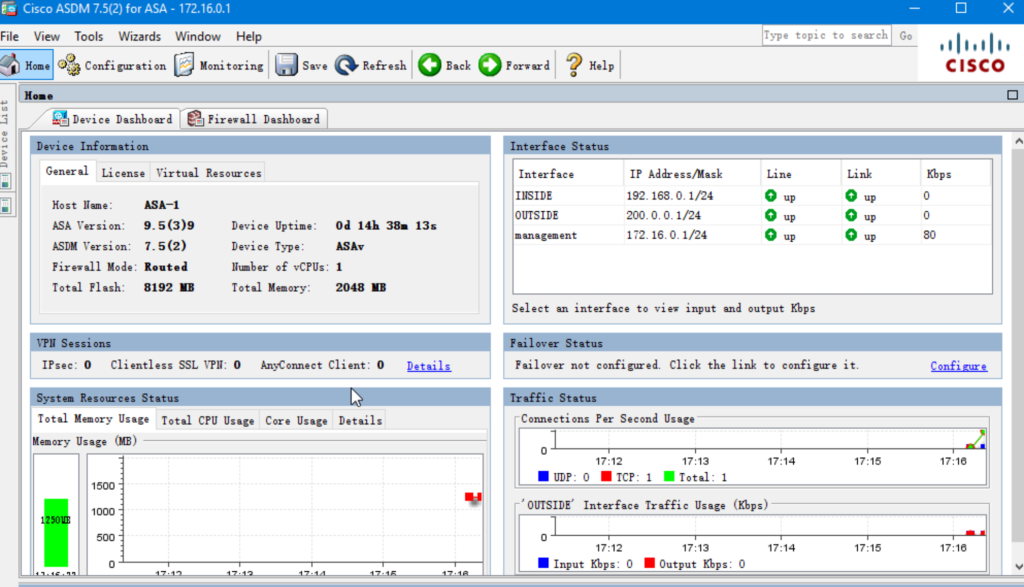
Debugging
we can check debugging for access management by enabling logging
logging on
logging buffered 7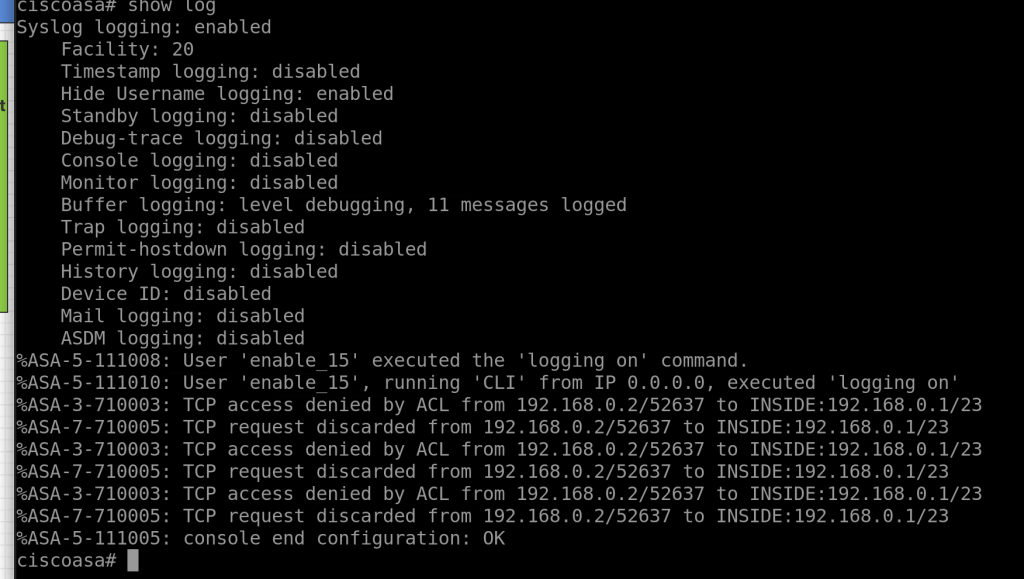
for example from this picture, we can see there is denied access to telnet access.
Some error when enabling ssh ASA
when client ssh try to ssh to ASA and failed to connect because this error
Connection to 200.0.0.1 aborted: error status 0]
R3#
*Oct 13 03:58:36.189: %SSH-3-NO_MATCH: No matching kex algorithm found: client diffie-hellman
-group-exchange-sha1,diffie-hellman-group14-sha1 server diffie-hellman-group1-sha1
R3#ssh -l cisco 200.0.0.1 workaround: set stronger ssh key to ASA
ssh key-exchange group dh-group14-sha1 Download ASDM client and java
if you dont have asdm client or java installed, you can download the java and ASDM client from browser and access ASA IP server