Overview Static NAT
- Static nat translate single real ip to single mapped ip address that is routable on destination network.
- mostly is used when outside network/internet want to access internal resources such as server.
- Static NAT is bidirectional.
Overview Static PAT
- Static PAT is uni-directional
- directions its depend on service object:
- if destination port is defined source IP will be translated.
- if source port is defined destination IP will be translated, mostly when you want to get access from outside to inside.
- Example Scenario:

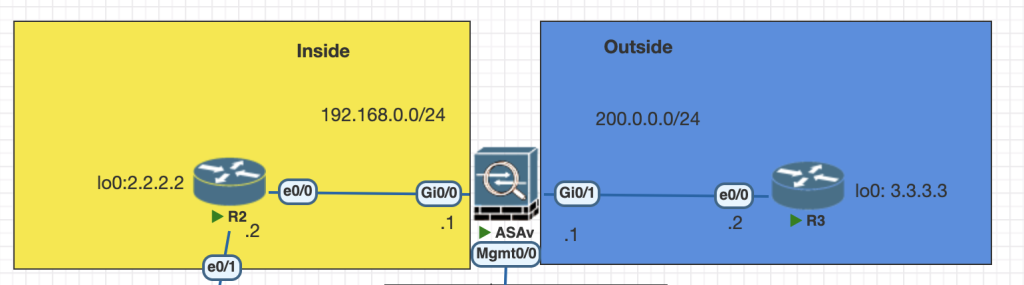
Topology
Testing Scenarios
- Web Server (loopback R2 ) 2.2.2.2 should be translated to a public IP address 200.0.0.50. Ensure that outside world can access your Web Server on its public IP address. Verify from R3, by doing HTTP to 200.0.0.50 on port 80. (Static NAT configurations)
- PAT Translate 192.168.0.2 to 200.0.0.111. This translation should only happen when 192.168.0.2 access any destination for http on the outside. (Static PAT uni-directional)
- When any source from the internet accesses the outside IP address of the ASAx1 for telnet, the ASAx1 should redirect that traffic to 192.168.0.2. (Static PAT uni-directional)
Configurations
Scenario 1
- Define object network
object network O-2.2.2.2
host 2.2.2.2
object network O-Public-200.50
host 200.0.0.502. Define policy NAT
nat (INSIDE,OUTSIDE) source static O-2.2.2.2 O-Public-200.50Scenario 2
- Define object network and service
object service http-80
service tcp destination eq www
object network O-Public-200.111
host 200.0.0.111 2. Deine Policy static NAT PAT uni-directional
nat (INSIDE,OUTSIDE) source static O-192.168.2 O-Public-200.111 service http-80 http-80Scenario 3
- Define object service
object service telnet-23
service tcp source eq telnet check the difference for incoming connection from internet to inside use source NAT to translate destination IP.
2. Define static PAT NAT
nat (INSIDE,OUTSIDE) source static O-192.168.2 interface service telnet-23 telnet-233. Because the traffic coming from lower security zone outside to higher security zone inside we need to define access list and apply into outside interface
access-list from-OUT-IN-Telnet extended permit tcp any host 192.168.0.2 eq telnet
access-group from-OUT-IN-Telnet in interface OUTSIDEVerifications
we can check verification using packet-tracer or access from outside network in this example from R3.
Scenario 1:
- Telnet from R3 to Public IP ASA
packet-tracer input outside tcp 3.3.3.3 12345 200.0.0.50 80
telnet 200.0.0.50 80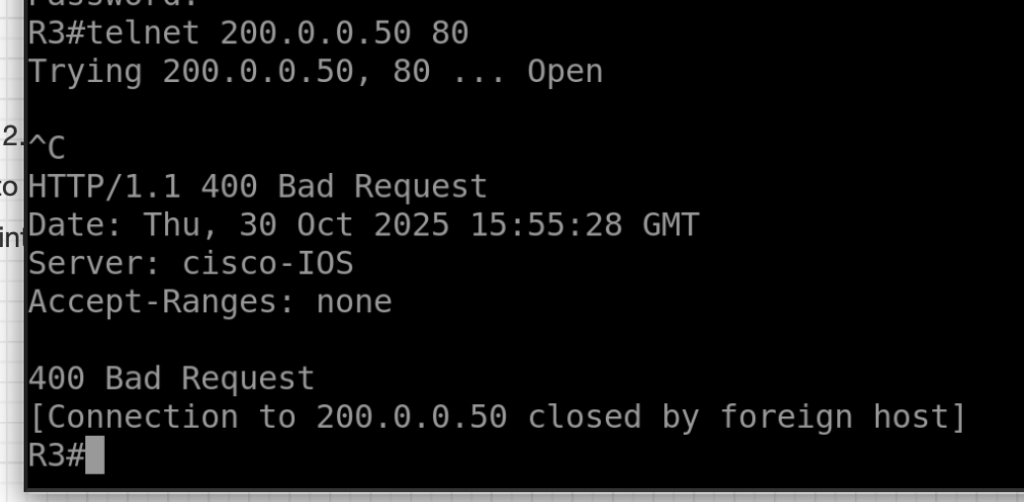
Scenario 2:
packet-tracer input inSIDE tcp 192.168.0.2 12345 3.3.3.3 80 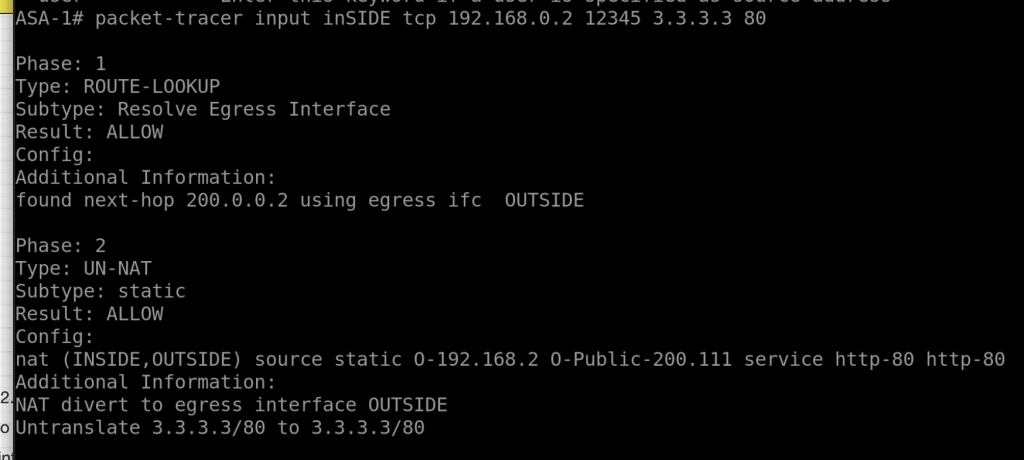
Scenario 3:
- we can use telnet and packet-tracer command to verify
packet-tracer input outside tcp 3.3.3.3 12345 200.0.0.1 23 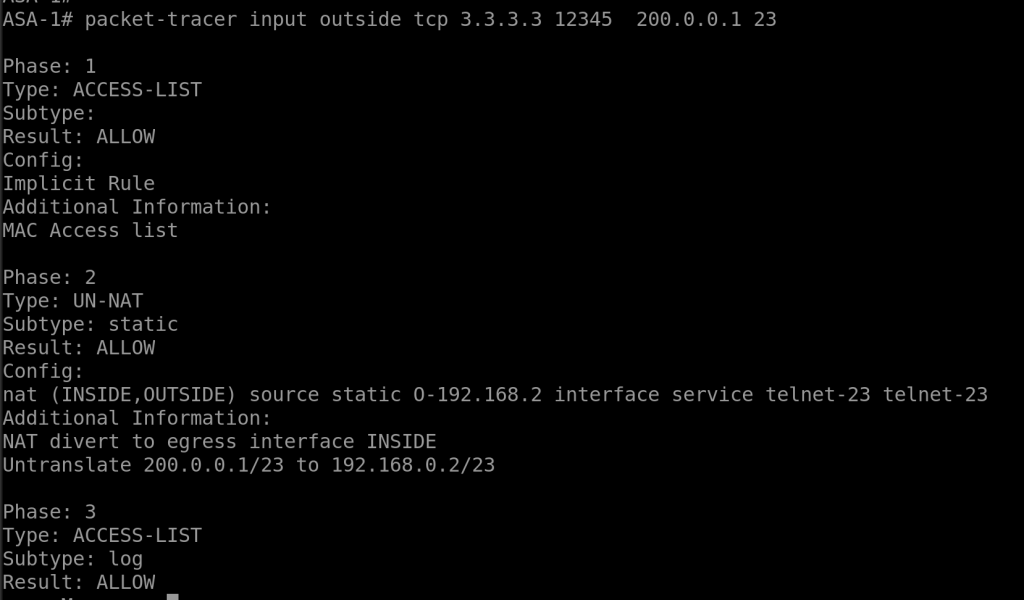
2. telnet to public ip ASA from R3
telnet 200.0.0.1 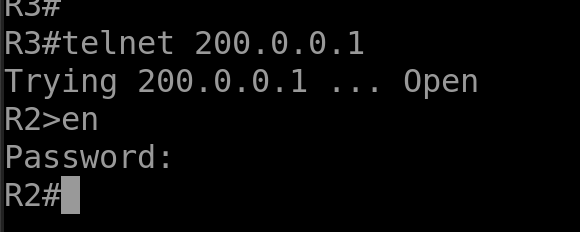
Conclusions
i had confusion in static PAT, because to define direction we need to change source/destination in service network. static PAT is uni-directional, the only way to change is via service network.
reminder for me:
Directions its depend on service object:
if destination port is defined source IP will be translated.
if source port is defined destination IP will be translated, mostly when you want to get access from outside to inside.
If you found this useful, subscribe to newsletter
