Overview
- Stateful failover will replicate all the session from active firewall it will ensure the user connection not interrupted.
- The health of active interfaces and unit is monitored to determine if specific failover conditions are met. If those meet the failover will occurs.
- ASA support fail-over mode:
- Active/Active: both of devices can pass traffic from user, with this we can load balance on your network. its only available on multiple context.
- Active/Standy: only single devices can pass traffic, other devices is standby. can work in single context or multiple context.
Requirements
- same hardware configurations
- same model
- same number and type interfaces and the same amount of RAM
- must be same operation modes (routed, transparent, single, multi context )
- same version major (first number) and minor (second number) number versions.
- we can have different version during upgrade process.
Failover links
- Two unit of devices will pair and communicate with fail over link. The ASA will use this failover link to sent informations:
- state (active,standby)
- power status
- hello-messages
- network link status
- mac address exchange
- configuration replication and synchronizations.
Stateful Failover links
- This link is used for replicating state
- can use dedicated ethernet link to stateful failover link
- if you are using LAN-Based, you can share the failover links.
Topology
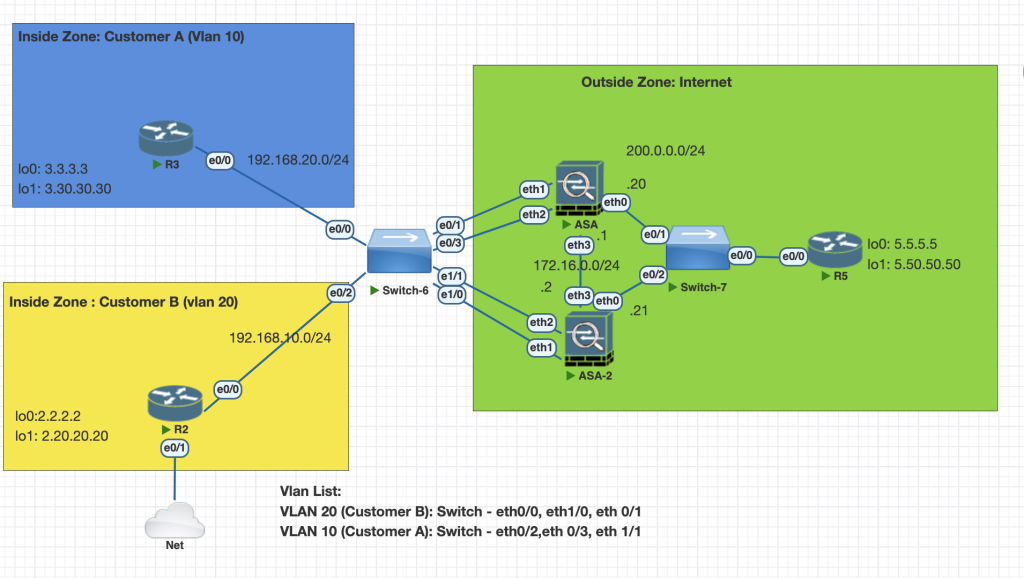
Testing Scenarios
- Configure Active/Standby for ASAx1 and ASAx2 for customer A and B
- Configure Active/Active failover with ASAx1 being active and ASAx2 being standby for CustomerA.
- Configure Active/Active failover with ASAx2 being active and ASAx1 being standby for CustomerB.
- IP address for Inside and Outside of CustomerA is 192.168.20.3 and 200.0.0.21 respectively.
- IP address for Inside and Outside of CustomerB is 10.0.2.61 and 200.0.0.11 respecttively.
Configurations
Scenario 1
before start configuring HA we need to make sure both of ASA run on the mode and make sure all the interface is up.
change ASAx2 to multicontext mode
config
mode multipleConfigure primary ASAx1 for HA
failover lan unit primary
failover lan interface Failover Ethernet3
failover link Failover Ethernet3
failover interface ip Failover 172.16.0.1 255.255.255.0 standby 172.16.0.2Configure Standby ASAx2
failover lan interface Failover Ethernet3
failover link Failover Ethernet3
failover interface ip Failover 172.16.0.1 255.255.255.0 standby 172.16.0.2
failover lan unit secondary
failoverStart sync HA from router ASAx1 with this comand
# start sync command
failover
# we can start to configure ip address standby ASA by changing to context customer A and customer B
changeto context CustomerA
!
interface Ethernet0
nameif OUTSIDE
security-level 0
ip address 200.0.0.20 255.255.255.0 standby 200.0.0.21
!
interface Ethernet1
nameif INSIDE
security-level 100
ip address 192.168.20.2 255.255.255.0 standby 192.168.20.3
ASA-1/CustomerA(config)#
# Customer B
interface Ethernet0
nameif OUTSIDE
security-level 0
ip address 200.0.0.10 255.255.255.0 standby 200.0.0.11
!
interface Ethernet2
nameif INSIDE
security-level 100
ip address 192.168.10.2 255.255.255.0 standby 192.168.10.3 Verifications
we can check our HA configuration is correct with this command
show failover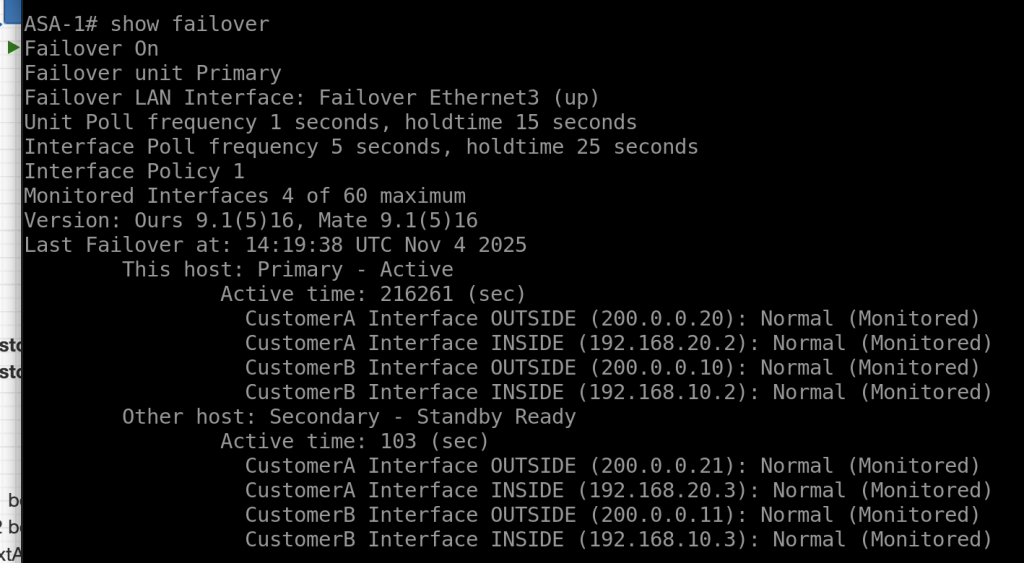
Scenario 2
To solve scenario 2 we need to create group failover
failover group 1
failover group 2change to configuration context and join the context to group failover
context CustomerA
join-failover-group 1
!
context CustomerB
join-failover-group 2
!Verifications
To verify HA active/active we can use command enter show failover on secondary node
show failover
# output
ASA-1# show failover
Failover On
Failover unit Secondary
Failover LAN Interface: Failover Ethernet3 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 60 maximum
Version: Ours 9.1(5)16, Mate 9.1(5)16
Group 1 last failover at: 02:29:06 UTC Nov 7 2025
Group 2 last failover at: 02:29:05 UTC Nov 7 2025
This host: Secondary <--- group 1 and group 2 are Standby status in Secondary Unit
Group 1 State: Standby Ready
Active time: 0 (sec)
Group 2 State: Standby Ready
Active time: 0 (sec)
CustomerA Interface OUTSIDE (200.0.0.21): Normal (Monitored)
CustomerA Interface INSIDE (192.168.20.3): Normal (Monitored)
CustomerB Interface OUTSIDE (200.0.0.11): Normal (Monitored)
CustomerB Interface INSIDE (192.168.10.3): Normal (Monitored)
Other host: Primary <--- group 1 and group 2 are Active status in Primary Unit
Group 1 State: Active
Active time: 391 (sec)
Group 2 State: Active
Active time: 391 (sec)
CustomerA Interface OUTSIDE (200.0.0.20): Normal (Monitored)
CustomerA Interface INSIDE (192.168.20.2): Normal (Monitored)
CustomerB Interface OUTSIDE (200.0.0.10): Normal (Monitored)
CustomerB Interface INSIDE (192.168.10.2): Normal (Monitored)
Stateful Failover Logical Update Statistics
Link : Failover Ethernet3 (up)
Stateful Obj xmit xerr rcv rerr 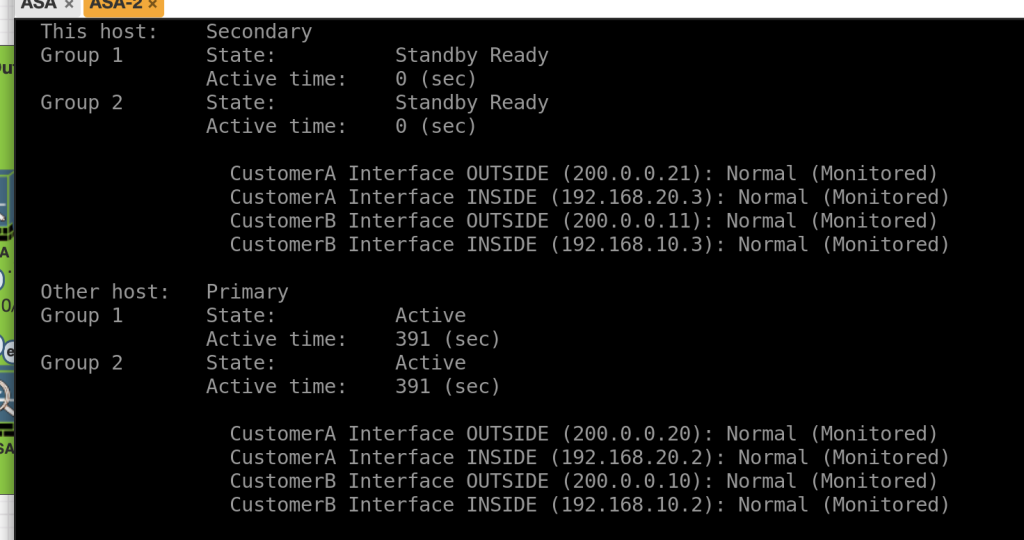
Conclusions
- to configure Active/Active on ASA first configure Active/Standby after that just create failover group and joined the context to the failover group.
- don forget to no shutdown interface for ethernet3 or all interface.
If you found this useful, subscribe to newsletter
