Overview
- Object or Object group are used to identify network or services.
- there are to objects that we can create:
- Network
- Service
- There are six type of object group that we can create
- network
- service
- protocol
- user
- icmp-type
- security
Topology
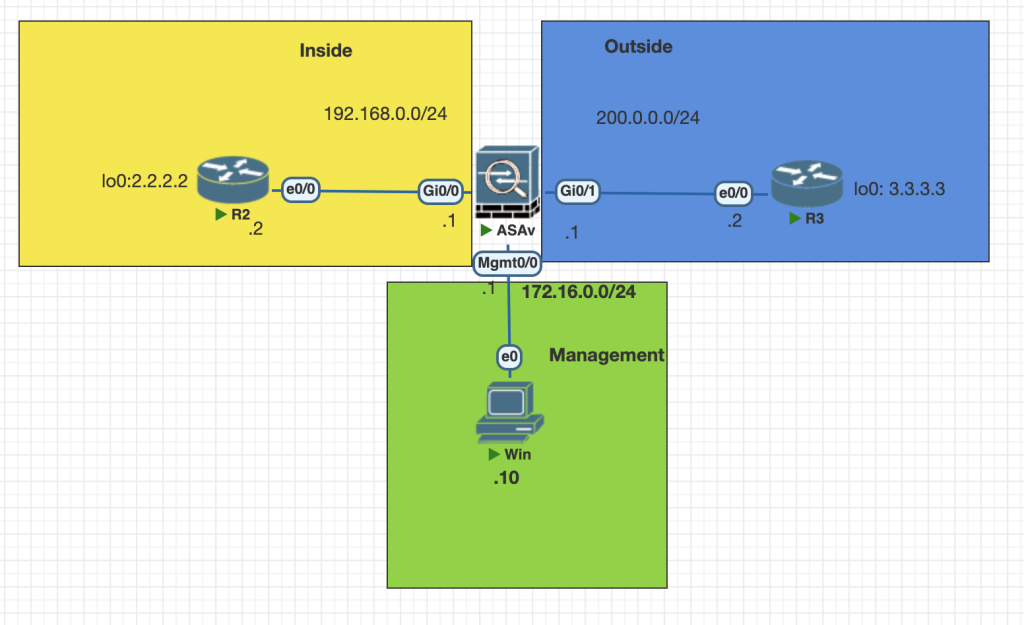
Testing Scenario
- Permit HTTP traffic from any source to destination host 192.168.0.2 Do not use any objects or object-group to achieve this requirement. Apply this ACL to OUTSIDE interface.
- Permit HTTP and Telnet from any source to destination network 192.168.0.0/24 and 2.2.2.2/32. Use object-groups to achieve this requirement. Apply this ACL to OUTSIDE interface.
- Permit HTTP, HTTPS and Telnet from any source to destination 2.2.2.2/32. Use objects to achieve this requirement. Apply this ACL to OUTSIDE interface.
- Permit udp 53 globally.
Configuration
Solutions Testing Scenario #1
set access list
access-list Permit-From-Outside extended permit tcp any host 192.168.0.2 eq www
apply the access list to the interface outbound
access-group Permit-From-Outside in interface OUTSIDEwe can testing connection from outside (R3) to inside (R2) network using this command
telnet 192.168.0.2 80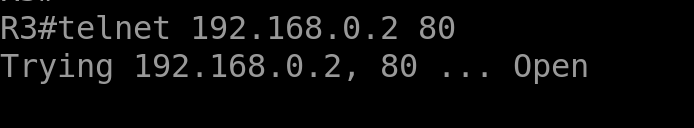
if we wan to theck the login we can enable buffered on show the log from console
logging on
logging buffered 7
show logging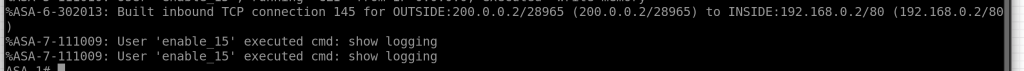
from the picture above we can see the connection is allowed from outside to inside ip address 192.168.0.2
Solutions Testing Scenario #2
define object group
object-group service G-insideService
service-object tcp destination eq www
service-object tcp destination eq telnet
object-group network G-InsideNetwork
network-object 192.168.0.0 255.255.255.0
network-object host 2.2.2.2create access list using the previous object group
access-list PermitTelnetHTTP extended permit object-group G-insideService any object-group G-InsideNetworkapply access list into the interface outbound
access-group PermitTelnetHTTP in interface OUTSIDETesting telnet from R3 to Inside network
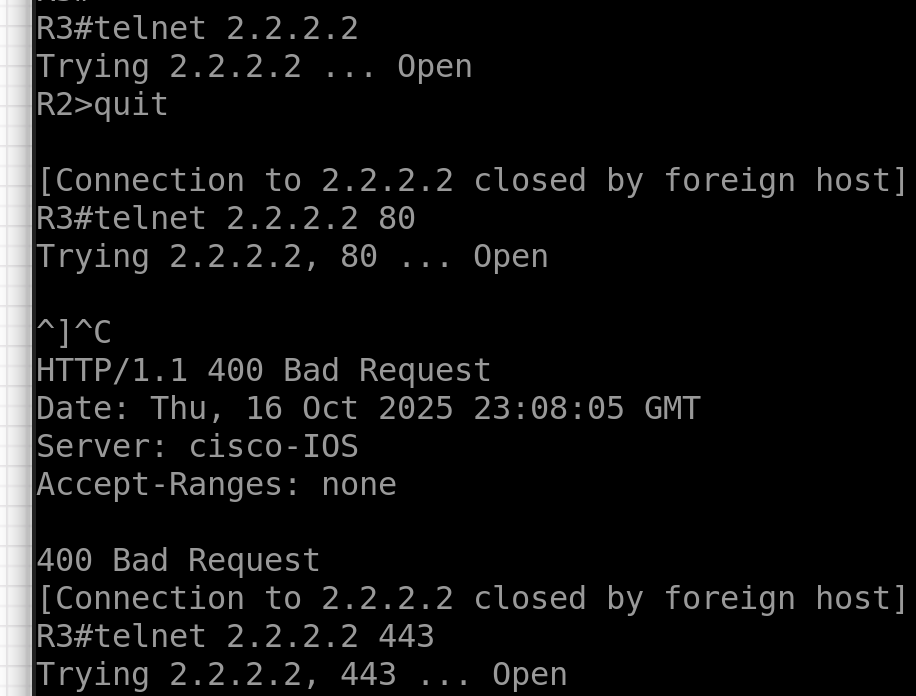
telnet 2.2.2.2 80
telnet 2.2.2.2 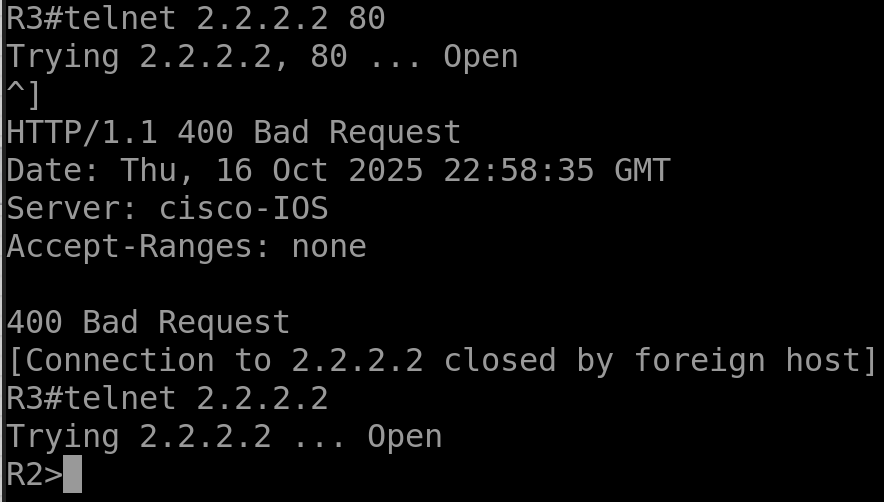
Solutions Testing Scenario #3
define object
object-group service InsideServiceAllow
service-object tcp destination eq www
service-object tcp destination eq https
service-object tcp destination eq telnet
object network internalServer
host 2.2.2.2define access list
access-list PermitInternalServer extended permit object-group InsideServiceAllow any object internalServer apply the access list into outside interface
access-group PermitInternalServer in interface OUTSIDEverify connection
Solutions Testing Scenario #4
in this scenario we will permit tcp service port 53 for any interface, first create the acl.
access-list permit-dns permit tcp any any eq domain apply into global config
access-group permit-dns global 