Overview
- Undirectional NAT (only source address is translated)
- NAT in ASA has section:
- Manual nat is configure in global config it will go to section 1.
- Auto NAT is configure in object config it will go to section 2.
- section 3 is configure in global config and its manual NAT.
- NAT sequence
- all traffic will inspect in section 1.
- if nat traffic not match section 1 it will go to section 2.
- if not match it will go section 3.
Topology
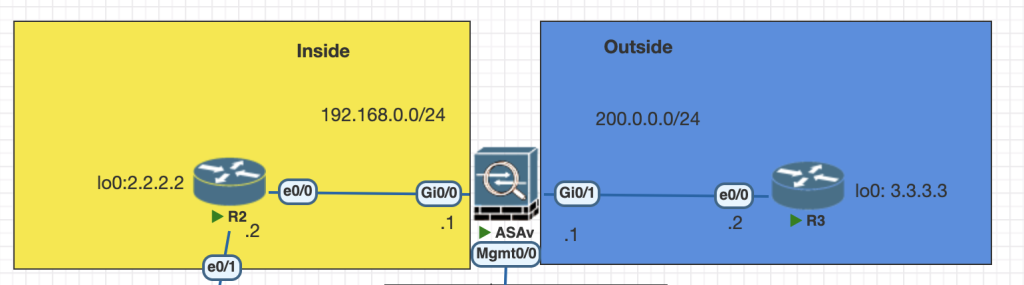
Testing Scenario
- All traffic from inside to outside must be dynamically translated to IP addresses ranging from 200.0.0.100 to 200.0.0.254 This rule should be configured globally.
- All traffic sourced from 192.168.0.0/24 to any destination on the outside must be translated using the range 200.0.0.98 to 200.0.0.99. If pool is full, then they should be translated using another pool of IP addresses ranging from 200.0.0.80 to 200.0.0.81. This rule should be configured globally.
- All traffic sourced from 2.2.2.2/32 to any destination on the outside must be translated using the range 200.0.0.70 to 200.0.0.75. This rule should not be configured globally.
Configuration
Before we start configuring the rule, we need to identify which NAT section each rule belongs to. We can identify or classify based on grannular rule or more specific rule.
- Scenario number 1 must belong to Section 3, because its default NAT.
- Scenario number 2 must belong to Section 1, because its specific and must configured on global config.
- Scenario number 3 must belong to section 2, because NAT it is included in object group
Configuration Scenario 1
- create object group
object network O-200.100-200.254
range 200.0.0.100 200.0.0.2542. define nat rule.
nat (INSIDE,OUTSIDE) after-auto source dynamic any O-200.100-200.2543. Verification
show nat
show run | b objectConfiguration Scenario 2
- create object group
object network O-192.168
subnet 192.168.0.0 255.255.255.0
object network pool1
range 200.0.0.98 200.0.0.99
object network pool2
range 200.0.0.80 200.0.0.81
object-group network all-pool
network-object object pool1
network-object object pool22. define nat Rule
nat (INSIDE,OUTSIDE) source dynamic O-192.168 all-pool3. Verification
show nat
show run | b objectConfiguration scenario 3
- define object directly define the nat policy in object network
object network Public-2.2.2.2
range 200.0.0.70 200.0.0.75
object network 2.2.2.2
host 2.2.2.2
nat (INSIDE,OUTSIDE) dynamic Public-2.2.2.2Verifications
we can verify nat rule using tools packet tracer command provide by cisco ASA, lets verify NAT for each scenario
show nat
Scenario 1
packet-tracer input inSIDE tcp 10.0.0.10 12345 3.3.3.3 80 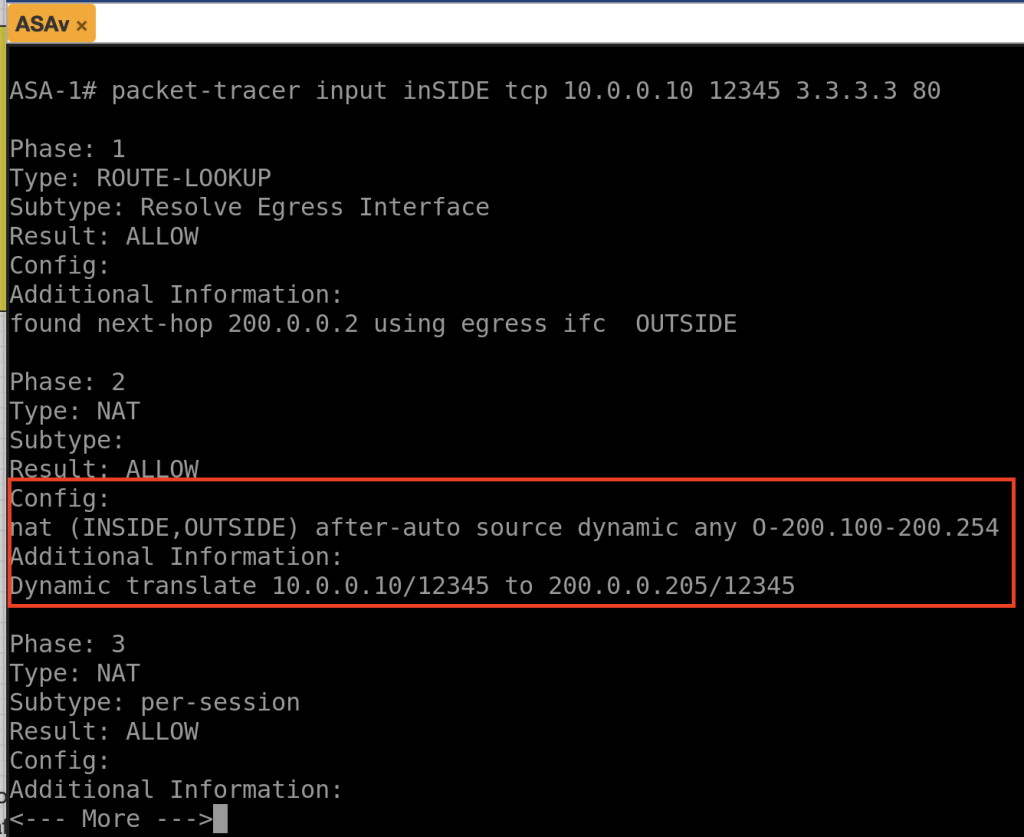
Scenario 2
packet-tracer input inSIDE tcp 192.168.0.10 12345 3.3.3.3 80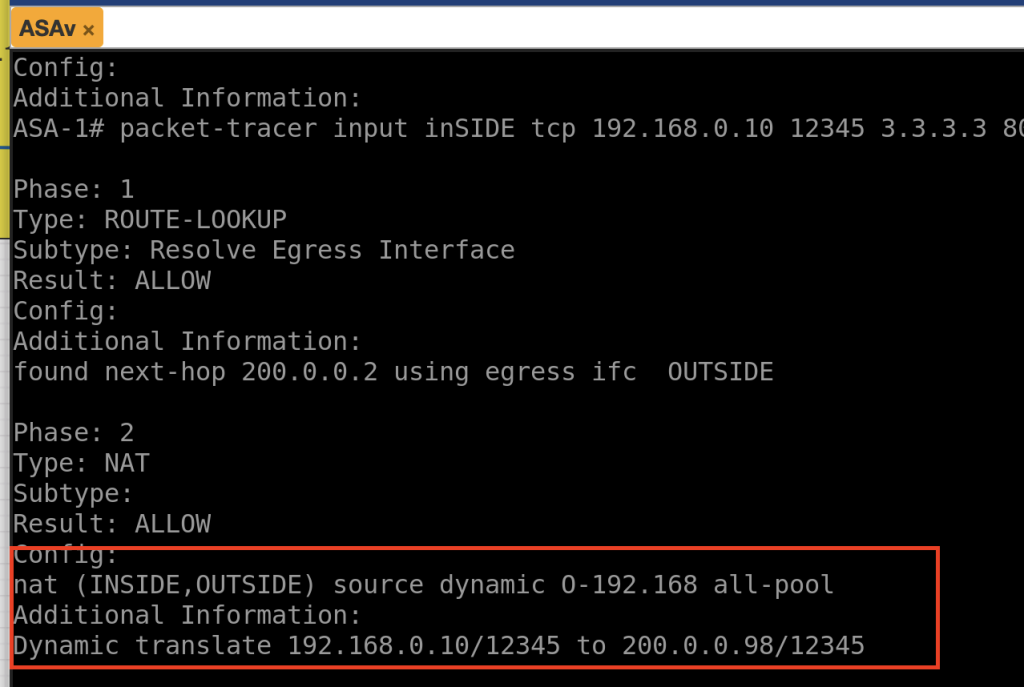
Scenario 3
packet-tracer input inSIDE tcp 2.2.2.2 12345 3.3.3.3 80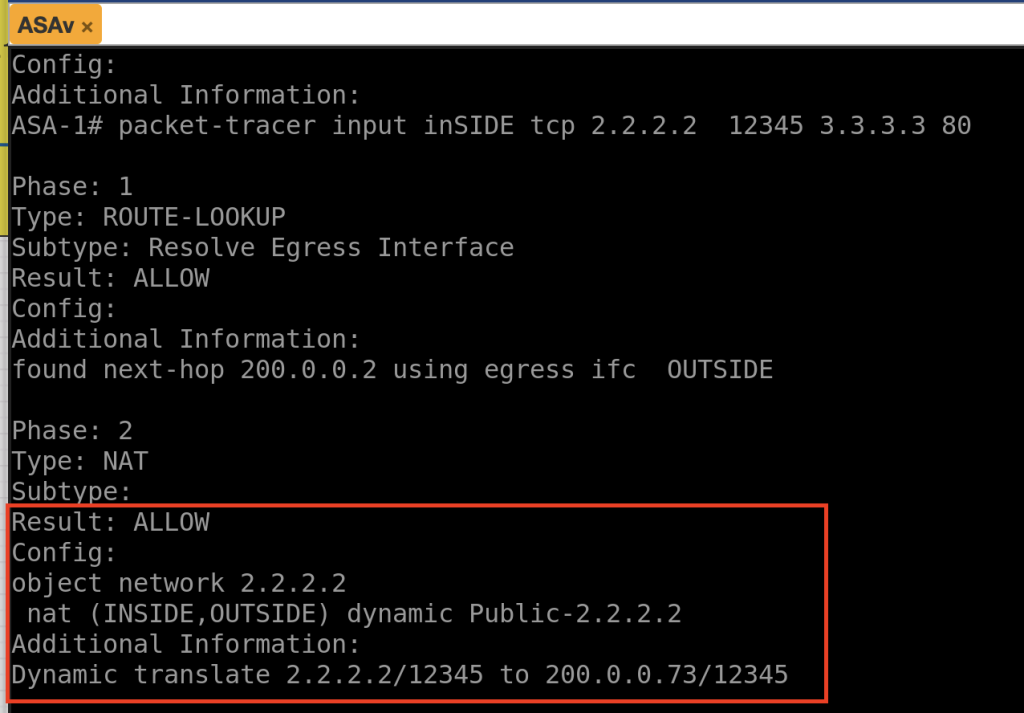
Conclusion
With dynamic NAT we can translate source ip address to other ip address, basically it used in private address accessing public network or Internet.
If you found this useful, subscribe to newsletter
